
The Cisco certifications are most renowned IT certifications which are highly regarded in organizations. The Cisco certification will endorse your skills as a Cisco network associate and your skills in networking, switches and routers. The CCNA exam needs not only training also a comprehensive exam preparation. We will support you by compiling CCNA exam question and answers which you can practice before giving your Cisco CCNA Exam. Hope these ccna practice test questions will help you to brush up your concepts and help you for the last minute quick preparation.
We have prepared these Cisco Certified Networking Associate certification exam dumps from a wide range of sources for reviewing from old to the updated questions. In this blog, you have the best 30 CCNA practice test questions with which you can study and pass exams faster. Candidates who are going to attend CCNA test can use these sample questions and answers as a study guide to understand for a deep dive to achieve passing score and to earn certification at the first try.
Exam Details: https://www.cisco.com/c/en/us/training-events/training-certifications/exams/current-list/200-125-ccna.html
Exam name: 200-125
Duration: 90 minutes
No. of questions: 60-70
Passing score: 80%
Validated against: Pearson VUE
Format: Multiple choices
Exam price: 325 USD
--------------------------------------------------------------------------------------------------------------------------
1. What technology allows an enterprise to more easily change their cloud provider (e.g. change from Microsoft to AWS)?
a. CloudFront
b. Intercloud Exchange
c. MP-BGP
d. APIC-EM
An enterprise can have a connection to an Intercloud Exchange provider, which has connections to multiple cloud providers. This allows the enterprise to switch to a different cloud provider while keeping their existing connection to the Intercloud Exchange.
-----------------------------------------------------------------------------------------------------------------------------
2. What Cisco technology allows you to interconnect multiple physical switches into a single logical switch?
a. SmartNet
b. Optimum Switching
c. StackWise
d. Collapsed Core
Cisco StackWise allows you to interconnect multiple Cisco Catalyst switches (that have Stackwise support) using special interconnect cables. You can then administer the stack of switches as one logical unit.
-------------------------------------------------------------------------------------------------------------------------------
3. What type of queuing adds a priority queue to CB-WFQ?
a. ECN
b. LLQ
c. WRED
d. WFQ
Low Latency Queuing (LLQ) allows you to place one or more types of priority traffic into a priority queue. Other traffic types can be placed into non-priority queues, which can be given minimum bandwidth guarantees. Note that the priority queue used by LLQ is policed (i.e. has a bandwidth limit).
--------------------------------------------------------------------------------------------------------------------------------
4. What network are architecture layers combined in a collapsed core design?
a. Access and Distribution
b. Distribution and Core
c. Access and Core
d. Access, Distribution, and Core
A Collapsed Core design is sometimes called a Two-Tier design, where the two tiers are the Access Layer and the Collapsed Core layer. This consolidated Collapsed Core layer combines the functions of the traditional Distribution and Core layers.
--------------------------------------------------------------------------------------------------------------------------------
5. Which of the following is considered to be an unreliable Transport Layer protocol?
a. IP
b. UDP
c. TCP
d. ICMP
e. PPP
IP (Internet Protocol) and ICMP (Internet Control Message Protocol) are Network Layer (i.e. Layer 3) protocols. Point-to-Point Protocol is a Data Link Layer (i.e. Layer 2) protocol.
Transmission Control Protocol (TCP) and User Datagram Protocol (UDP) are both Transport Layer (i.e. Layer 4) protocols. However, TCP uses acknowledgements to confirm receipt of data, while UDP does not confirm receipt of data. Therefore, TCP is considered to be a reliable, connection-oriented protocol, while UDP is considered to be an unreliable, connectionless protocol.
--------------------------------------------------------------------------------------------------------------------------
6. Which of the following are dynamic routing protocols? (Choose 2.)
a. ICMP
b. OSPF
c. SNMP
d. ARP
e. EIGRP
OSPF (Open Shortest Path First) is a distance-vector dynamic routing protocol that uses the Dijkstra Shortest Path First Algorithm to determine the best path to a remote network.
Enhanced Interior Gateway Routing Protocol is an advanced distance-vector dynamic routing protocol that uses the Diffusing Update Algorithm to determine the best path to a remote network.
------------------------------------------------------------------------------------------------------------------------------
7. What is the default hold time for HSRP?
a. 1-second
b. 3 seconds
c. 5 seconds
d. 10 seconds
By default, Hot Standby Router Protocol (HSRP) has a default Holdtime timer value of 10 seconds. The default Hello timer value is 3 seconds. Also, there is a requirement that the value of the Holdtime timer is at least three times the value of the Hello timer.
---------------------------------------------------------------------------------------------------------------------------
8. What Cisco technology allows you to interconnect multiple physical switches into a single logical switch?
a. SmartNet
b. Optimum Switching
c. StackWise
d. Collapsed Core
Cisco StackWise allows you to interconnect multiple Cisco Catalyst switches (that have Stackwise support) using special interconnect cables. You can then administer the stack of switches as one logical unit.
--------------------------------------------------------------------------------------------------------------------------------
9. When an interface is configured with Port Fast BPDU guard, how does the interface respond when it receives a BPDU?
A. Normal operations are continued.
B. Experiences a down/down state
C. Acts as the root bridge for the configured VLAN.
D. An errdisable state is experienced
The interface goes into an errdisable state when it receives a BPDU state. The errdisable state is a feature which disables a port on Cisco Catalyst switch. When the port error is disabled, there will be no receive or sent, and it will be a total shut down.
--------------------------------------------------------------------------------------------------------------------------
10. Which condition does the err-disabled status indicate on an Ethernet interface?
A. There is a duplex mismatch.
B. The connection is without power for the device.
C. The serial interface is disabled.
D. The Configuration comes with the shutdown command.
E. Port security has disabled the interface.
F. The interface is fully functioning
On the errdisabled status on the Ethernet interface disables the port security.
--------------------------------------------------------------------------------------------------------------------------------
11. Which statement about RADIUS security is true?
A. It supports EAP authentication for connecting to wireless networks.
B. It provides encrypted multiprotocol support.
C. Device-administration packets are encrypted in their entirety.
D. It ensures that user activity is entirely anonymous.
The RADIUS (Remote authentication dial-in user service) provides security against unauthorised access. It provides AAA (authentication, authorisation and accounting. Hence, the statement that RADIUS supports EAP authentication to connect wireless networks is correct.
-------------------------------------------------------------------------------------------------------------------------------
12. What kind of devices are replaced by the use of subinterfaces or VLAN routing?
A. Layer 2 bridge
B. Layer 2 switch
C. Layer 3 switch
D. router
Layer 3 Switch makes VLAN and inter VLAN routing easy and straightforward. The routing is made possible on the switch itself. A separate router is not required between each VLAN.
--------------------------------------------------------------------------------------------------------------------------------
13. Which function of the IP SLAs ICMP jitter operation can you use to determine whether a VoIP issue is caused by excessive end-to-end time?
A. Packet loss
B. jitter
C. successive packet loss
D. Round-trip time latency
The Round-trip time latency determines the excessive end-to-end time. Round trip latency is the time required for the data to travel from one end to the other end of the network.
--------------------------------------------------------------------------------------------------------------------------------
14. What are the two options which are justified o use an IPV4 private IP space?
A. To enable intra-enterprise communication
B. To conserve global address space
C. To manage routing overhead
D. To connect applications
E. To implement NAT
The IPV4 Private IP space is used to enable intra-enterprise communication and to conserve global address space.
--------------------------------------------------------------------------------------------------------------------------------
15. Which three statements about DWDM are true?
A. A single strand of fibre supports Bi-Directional communication.
B. DWDM is helpful in submarine long-distance cable-systems
C. DWDM can multiplex up to 256 channels on a single fibre
D. DWDM supports both the SDH and SONET standards
E. 1 Gbps signals.
F. DWDM supports simplex communications over multiple strands of fibre
The Dense wavelength division multiplexing is a fibre optic transmission technique. The multiplexing can be done up to 256 channels on a single fibre and supports both SDH and SONET standards. Up to 1Gbps signal is carried by each channel.
--------------------------------------------------------------------------------------------------------------------------------
16. Which functionality does an SVI provide?
A. OSI Layer 2 connectivity to switches
B. Remote switch administration
C. Traffic routing for VLANs
D. OSI Layer 3 connectivity to switches
The virtual switch interface (SVI) provides traffic routing for VLANs. The SVI delivers layer three processing from all switch ports linked to VLANs.
--------------------------------------------------------------------------------------------------------------------------------
17. Which is true regarding DHCP snooping?
A. Traffic gets blocked from DHCP servers on untrusted interfaces.
B. DHCP can be configured on switches and routers.
C. It allows packets from untrusted ports if their source MAC address is found in the binding table.
D. It uses DHCP Discover packets to identify DHCP servers
Dynamic host configuration protocol provides IP and blocks traffic from untrusted interfaces.
--------------------------------------------------------------------------------------------------------------------------------
18. What id of the cable is used to connect two devices with MDI interfaces?
A. rolled
B. crossover
C. crossed
D. straight through
A medium dependent interface is referred to an Ethernet port connection which connects network devices with other hubs and switches. It uses a crossover cable.
--------------------------------------------------------------------------------------------------------------------------------
19. Name the highest layer of the protocol stack that the network administrator while verifying a new host?
A. An Application
B. The Presentation
C. The Session
D. Transport
E. An Internet
F. The Datalink
The Application is the highest layer of the protocol stack that the network administrator uses.
----------------------------------------------------------------------------------------------------------------------------
20. What are the two results that would occur if the hub is replaced with a switch that is configured with one Ethernet VLAN?
A. There is no change in the number of the collision.
B. There is a decrease in the collision domain.
C. An increase in the number of collisions is seen.
D. There is no change in the number of broadcast domains.
E. The broadcast domains will increase in number.
When a hub is replaced with a switch which is configured with Ethernet VLAN, the no. of collisions will increase, and the no. of broadcast domains will remain the same.
--------------------------------------------------------------------------------------------------------------------------------
21. A receiving host calculates the checksum on a frame and concludes that the frame is damaged and discards. At which OSI layer did this happen?
A. session
B. transport
C. network
D. data link
E. physical
The frame is damaged and discarded on data link OSI layer.
-----------------------------------------------------------------------------------------------------------------------------
- Mention the steps in the OSI data encapsulation process?
A. The data stream is divided into segments and adds dependability and the flow of data.
B. The data link and an FCS add the Physical source and destination addresses.
C. Packets are created when the network layer summarises with the source, destination addresses and other information regarding protocol control
D. When the Layer 3 addresses and control information is added to the network layer, packets are created.
E. The bits get translated to voltages by presentation layer presentation layer across the physical link.
The transport layer is fragmented into segments and adds dependability and data flow. The packets are created when the layer 3 controls information and adds to the network layer.
-------------------------------------------------------------------------------------------------------------------------------
23. Explain how two ethernet interfaces connect to four VLAN with few physical interfaces and without a reduction in the network performance?
A. Connect the four VLANs with a swift Ethernet interface by using a hub on the router.
B. Handle VLAN traffic with the second router.
C. An Addition of two more Fast Ethernet interfaces.
D. Implement a router-on-a-stick configuration.
The two fast Ethernet interfaces can be connected to four VLANs by implementing a router-on-a-stick configuration.
-------------------------------------------------------------------------------------------------------------------------
24. Determine the layer in the OSI reference model responsible for checking the availability of the receiving program if enough resources exist for that communication?
A. Transport
B. Network
C. Presentation
D. Session
E. Application
The application layer is responsible for determining the availability of receiving the program.
--------------------------------------------------------------------------------------------------------------------------
25. A frame was found damaged and discarded when a receiving host computes the checksum. At which OSI layer did this happen?
A. session
B. transport
C. network
D. data link
E. physical
The computed checksum on a frame which is damaged. This happened at data link on the OSI layer.
--------------------------------------------------------------------------------------------------------------------------------
26. Within the DoD TCP/IP reference model, Where does routing occur?
A. The Application
B.The Internet
C. The Network
D. Transport
The routing occurs within the DoD TCP/IP reference model on the internet.
-------------------------------------------------------------------------------------------------------------------------------
27. What are the different parameters on ports within an Ether Channel?
A. speed
B. DTP negotiation settings
C. trunk encapsulation
D. duplex
The DTP negotiation settings can be different in ports within the Ether Channel.
-----------------------------------------------------------------------------------------------------------------------------
28. The OSI model in RSTP used to prevent loops at which layer?
A. physical
B. data link
C. network
D. transport
The RSTP operates at OSI layer 2(data link level)
--------------------------------------------------------------------------------------------------------------------------------
29. The VLAN operation on switches, is correct in which statement?
A. The VLAN ID can be obtained from the MAC address source and the MAC address table.
B. Stranger unicast frames get transmitted to the ports belonging to the VLANs.
C. Retransmission of broadcast and multicast frames configured on different VLANs
D. The VLAN operation spans across ports which configure in access modes.
Th VLAN operation on switches is possible when retransmission of unicast frames is done to the same VLAN.
---------------------------------------------------------------------------------------------------------------------------
30. What is known as "one-to-nearest" addressing in IPv6?
A. Global unicast
B. Anycast
C. Multicast
D. Unspecified address
Anycast is a single destination address which has multiple routing paths. It is also known as one-to-nearest.
--------------------------------------------------------------------------------------------------------------------------------
31. OSPG has a default administrative distance of
A. 90
B. 100
C. 110
D. 120
The default administrative distance of OSPF had default administrative distance of 110.
--------------------------------------------------------------------------------------------------------------------------------
32. Which command encrypts all plaintext passwords?
A. Router# service password-encryption
B. Router (config) # password-encryption
C. Router (config) # service password-encryption
D. Router# password-encryption
The command used to encrypt plaintext passwords is Router (config) # service password-encryption.
--------------------------------------------------------------------------------------------------------------------------------
33. What is the Cisco name for encapsulation type used on a serial interface?
A. HDLC
B. SDLC
C. SAP
D. SNAP
The HDLC (High-level data link) is a cluster of rules used for transmitting data between nodes. This protocol ensures error-free transmission.
-------------------------------------------------------------------------------------------------------------------------------
34. Which Netware protocol provides link-state routing?
A.NLSP
B. RIP
C. SAP
D. NCP
A Netware link services protocol provides link-state routing.
------------------------------------------------------------------------------------------------------------------------------
35. Which of these statements are correct about PPP and SLIP for WAN communication?
A. PPP uses network control programs (NCCP) component to encapsulate multiple protocols
B. PPP can only transport TCP/IP
C. SLIP can just transport TCP/IP
D. SLIP uses its network control programs components to encapsulate multiple protocols.
The PPP (point-to-point protocol )is a communication protocol used to establish a link between two nodes. It uses NCCP. A SLIP (serial line internet protocol) transmits serial connections. It can transport TCP/IP.
------------------------------------------------------------------------------------------------------------------------------
36. Identify the purpose of the wildcard mask?
A. Match a particular portion of the IP address while ignoring the rest of the address.
B. Determine the class of IP address
C. Determine the network portion of Internet protocol
D. The IP address of the host part is hidden.
The purpose of wildcard mask is to match a particular portion of the IP address while ignoring the rest.
---------------------------------------------------------------------------------------------------------------------------
37. Identify the OSI layer associated with bits?
A. Physical
B. Network
C. Binary
D. Data link
In the seven-layer OSI, the physical layer is the first and the lowest layer. This layer decides how to transmit the raw bits over physical data links.
---------------------------------------------------------------------------------------------------------------------------
38. Identify the routing protocol that maintains a topological database of the network?
A. Topological state
B. Shortest path first
C. Link state
D. Distance vector
The link state routing protocol maintains a database that lists all the networks in the internetwork.
-----------------------------------------------------------------------------------------------------------------------------
39. What parameter is used with statistically assigned routers to tell packets which interface to use to reach a distant network?
A. Mask
B. Subnet
C. Default gateway
D. Interface
The interface parameter tell a packet which interface to use to reach other networks
----------------------------------------------------------------------------------------------------------------------------
40. Which of the following describe the full-duplex transmission
A. Uses a single wire
B. Data transmission in both directions but only one way at a time
C. Uses a point-to-point connection from the transmitter to the transmitter station to the receiver of the receiving station
D. Data transmission in only one direction
Full duplex, capability for simultaneous data transmission between a sending station and receiving station. It requires a workstation to be attached to a switch, the NIC must support it, and collision detection and loop back must be disabled.
--------------------------------------------------------------------------------------------------------------------------------
Find a course provider to learn CCNA
Java training | J2EE training | J2EE Jboss training | Apache JMeter trainingTake the next step towards your professional goals in CCNA
Don't hesitate to talk with our course advisor right now
Receive a call
Contact NowMake a call
+1-732-338-7323Take our FREE Skill Assessment Test to discover your strengths and earn a certificate upon completion.
Enroll for the next batch
CCNA Custom & real-time curriculum
- Dec 15 2025
- Online
CCNA Custom & real-time curriculum
- Dec 16 2025
- Online
CCNA Custom & real-time curriculum
- Dec 17 2025
- Online
Cisco Certifications ccna
- Dec 18 2025
- Online
Cisco Certifications ccna
- Dec 19 2025
- Online
Related blogs on CCNA to learn more

The Cisco Certified Network Associate (CCNA) Median Salaries: A Path to High-Earning Potential
The Cisco Certified Network Associate (CCNA) certification is one of the most widely recognized and respected credentials in the IT and networking industry. Holding a CCNA not only opens up a variety of career opportunities but also ensures a competi

What is a CISCO Packet Tracer?
Explore the functionalities and features of Cisco Packet Tracer, a network simulation tool by Cisco Systems, enabling users to design, build, and troubleshoot networks virtually in a safe and interactive environment, enhancing hands-on networking ski

What Is the CCNA?
What Is the CCNA? The CCNA, or Cisco Certified Network Associate, is a renowned certification offered by Cisco Systems, a leading networking solutions provider. This certification is a cornerstone in information technology and networking, validating

What’s CCNA and what are the new replacements
The New CCNA is designed in such a way it includes security, automation and programmability. It also covers a wide range of fundamentals under one exam, one training course. The following topics are included in the new CCNA certification
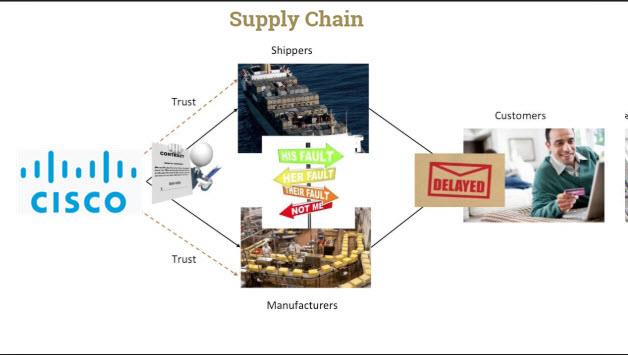
Cisco future shines high in china, the new supply chain winner
“I am proud to work on a team where I can contribute my expertise on environmental management and make full use of Cisco’s buying power to drive key stakeholders within our supply chain to protect the living environment when producing Cisco products,
Latest blogs on technology to explore

From Student to AI Pro: What Does Prompt Engineering Entail and How Do You Start?
Explore the growing field of prompt engineering, a vital skill for AI enthusiasts. Learn how to craft optimized prompts for tools like ChatGPT and Gemini, and discover the career opportunities and skills needed to succeed in this fast-evolving indust

How Security Classification Guides Strengthen Data Protection in Modern Cybersecurity
A Security Classification Guide (SCG) defines data protection standards, ensuring sensitive information is handled securely across all levels. By outlining confidentiality, access controls, and declassification procedures, SCGs strengthen cybersecuri

Artificial Intelligence – A Growing Field of Study for Modern Learners
Artificial Intelligence is becoming a top study choice due to high job demand and future scope. This blog explains key subjects, career opportunities, and a simple AI study roadmap to help beginners start learning and build a strong career in the AI

Java in 2026: Why This ‘Old’ Language Is Still Your Golden Ticket to a Tech Career (And Where to Learn It!
Think Java is old news? Think again! 90% of Fortune 500 companies (yes, including Google, Amazon, and Netflix) run on Java (Oracle, 2025). From Android apps to banking systems, Java is the backbone of tech—and Sulekha IT Services is your fast track t
From Student to AI Pro: What Does Prompt Engineering Entail and How Do You Start?
Learn what prompt engineering is, why it matters, and how students and professionals can start mastering AI tools like ChatGPT, Gemini, and Copilot.

Cyber Security in 2025: The Golden Ticket to a Future-Proof Career
Cyber security jobs are growing 35% faster than any other tech field (U.S. Bureau of Labor Statistics, 2024)—and the average salary is $100,000+ per year! In a world where data breaches cost businesses $4.45 million on average (IBM, 2024), cyber secu

SAP SD in 2025: Your Ticket to a High-Flying IT Career
In the fast-paced world of IT and enterprise software, SAP SD (Sales and Distribution) is the secret sauce that keeps businesses running smoothly. Whether it’s managing customer orders, pricing, shipping, or billing, SAP SD is the backbone of sales o

SAP FICO in 2025: Salary, Jobs & How to Get Certified
AP FICO professionals earn $90,000–$130,000/year in the USA and Canada—and demand is skyrocketing! If you’re eyeing a future-proof IT career, SAP FICO (Financial Accounting & Controlling) is your golden ticket. But where do you start? Sulekha IT Serv

Train Like an AI Engineer: The Smartest Career Move You’ll Make This Year!
Why AI Engineering Is the Hottest Skillset Right Now From self-driving cars to chatbots that sound eerily human, Artificial Intelligence is no longer science fiction — it’s the backbone of modern tech. And guess what? Companies across the USA and Can
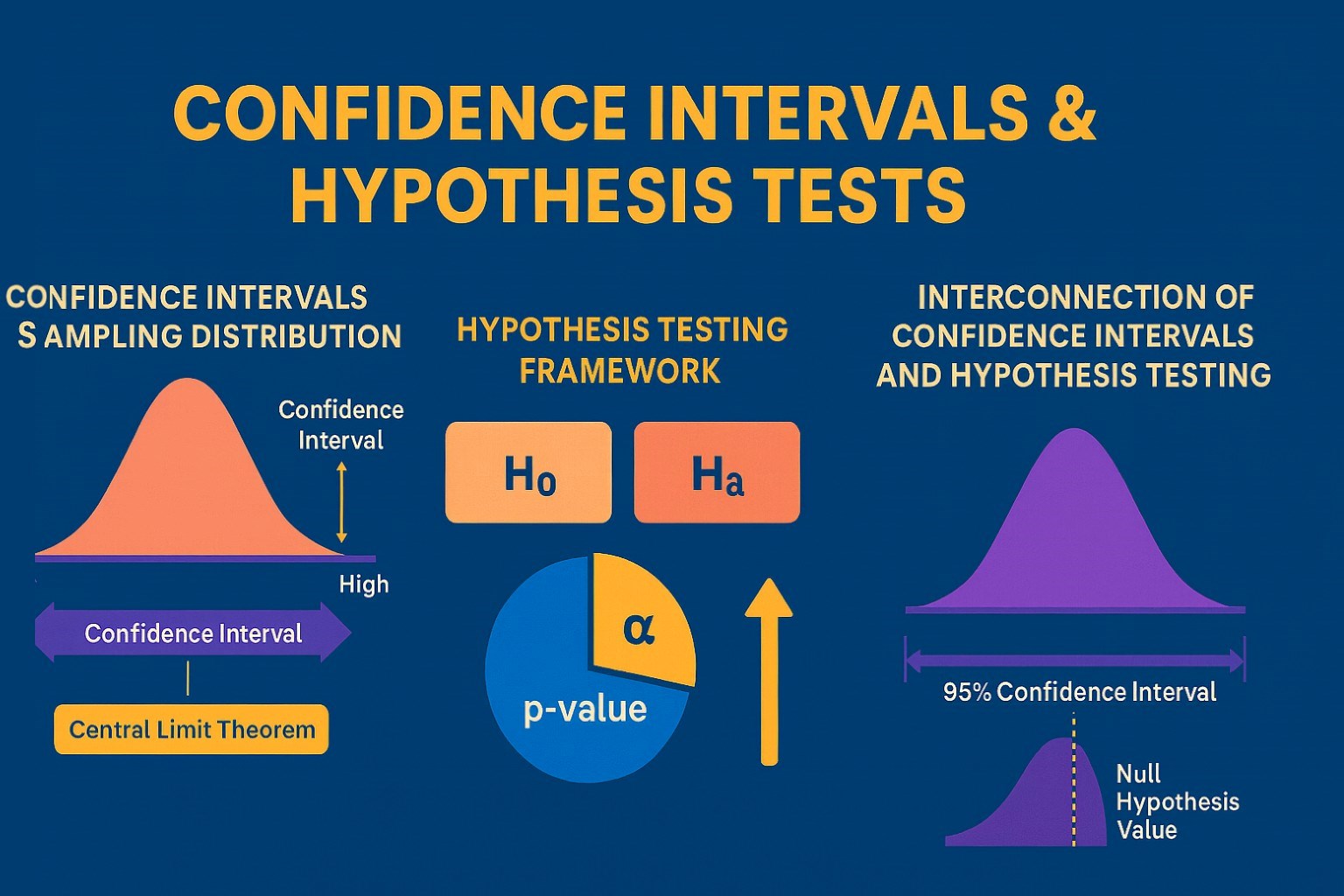
Confidence Intervals & Hypothesis Tests: The Data Science Path to Generalization
Learn how confidence intervals and hypothesis tests turn sample data into reliable population insights in data science. Understand CLT, p-values, and significance to generalize results, quantify uncertainty, and make evidence-based decisions.