Advancements in Cybersecurity technology to security 2.0

Among various emerging technologies, cybersecurity is an ever-proliferating career path for professionals and beginners. Moreover, cybersecurity is under immense pressure to move from signature-based detection methods to Behavioral Analytics.
In the old method or technique, security protection or hardening infrastructure security has failed to protect the data. On the other hand, having many layers to protect the organization even failed from security or data breaches.
As digital usage increases, zero vulnerabilities and social engineering are impossible, but it is significant contributors to these attacks. Cyberattacks are becoming more expensive as well. IBM revealed 2018 that the average cost of a cyberattack worldwide was USD 3,860,000. This price included costs for things like legal fees and clientele losses.
Anomaly-based Computer security systems
Cybersecurity tools have been updated and enable them to scan the traffic activity and ensure no malicious activities in the patterns.
This is a significant advantage for organizations moving from signature-based to anomaly-based detection.
For example, firewalls aid in finding or detecting malicious activities in the server and analyze whether servers accept multiple connections from new clients at a higher rate than average.
This would indicate that the connections were fraudulent and originated from a botnet. These connections would, therefore, be terminated. Many cybersecurity vendors developed tools that let organizations analyze real-time threats, thus thwarting attacks from unknown attack vectors.
On the other hand, Anomaly-based security tools have solved various security-related problems. Cybersecurity tools initially aid in finding malicious activities and provide threat reports to take necessary measures to protect the system or network.
These threat-analyzing tools could have been more efficient in securing or determining threats previously and providing active measures initially.
False positives were making the security tools unreliable. The introduction of anomaly-based security tools helps in analyzing real threats and how to stop cyber attacks.
Additionally, anomaly-based computer security systems made detection easier and more accessible. Initially, cybersecurity tools had to check with many signatures, which slowed network and system performance. On the other hand, Anomaly-based tools analyze real-time threats and evaluate whether traffic or apps have abnormal behavior.
Lastly, anomaly-based tools aid in encountering many social engineering attacks. These tools read packet headers to determine the origin and destination IP addresses, allowing traffic from known sources to pass through. Traffic from unknown sources was subjected to extensive checks to determine whether the origin had been blacklisted or reported as malicious by other security tools.
In conclusion, the advancements in cybersecurity technology have paved the way for Security 2.0, offering a range of innovative solutions that provide enhanced protection and peace of mind. These advancements have revolutionized the security landscape from biometric authentication to artificial intelligence-powered surveillance systems. With improved threat detection, faster response times, and increased efficiency, Security 2.0 is poised to address the evolving challenges of the digital age. As technology continues to evolve, we can expect further advancements in Security 2.0, ensuring a safer and more secure future for individuals, organizations, and society.
Find a course provider to learn Cyber Security
Java training | J2EE training | J2EE Jboss training | Apache JMeter trainingTake the next step towards your professional goals in Cyber Security
Don't hesitate to talk with our course advisor right now
Receive a call
Contact NowMake a call
+1-732-338-7323Take our FREE Skill Assessment Test to discover your strengths and earn a certificate upon completion.
Enroll for the next batch
Cyber Security Online Training
- Nov 6 2025
- Online
Cyber Security Online Training
- Nov 7 2025
- Online
Related blogs on Cyber Security to learn more

What Is a Security Classification Guide in Cybersecurity?
A Security Classification Guide (SCG) defines how to categorize information assets by sensitivity, with clear instructions from authorized officials to ensure consistent, compliant data handling.

Cybersecurity Training: Powering Digital Defense
Explore top cybersecurity training programs in the USA to meet rising demand in digital defense. Learn about certifications, salaries, and career opportunities in this high-growth field.

What Does a Cybersecurity Analyst Do? 2025
Discover the vital role of a Cybersecurity Analyst in 2025, protecting organizations from evolving cyber threats through monitoring, threat assessment, and incident response. Learn about career paths, key skills, certifications, and why now is the be

What essential skills and trends should cybersecurity professionals navigate in 2024?
Cybersecurity professionals in 2024 must master a diverse skillset, from cloud security and AI to soft skills like communication and problem-solving, to stay ahead of evolving cyber threats and regulations.

What Does a Cybersecurity Analyst Do?
Learn about the role of a Cybersecurity Analyst, responsible for protecting an organization's computer networks from cyberattacks.

10 Popular Cybersecurity Certifications
From CompTIA Security+ to CISSP, these certifications can boost your career and demonstrate your commitment to protecting computer systems and networks.

What are the most popular technical certifications for future career advancement?
Unlock your potential with insights into 5 popular technical certifications for future career growth, spanning cybersecurity, blockchain, cloud computing and more. Explore pathways for professional advancement today.

How to Become a Security Architect: 2024 Career Guide
How to Become a Security Architect: 2024 Career Guide In today's fast-paced and digitally interconnected world, the role of a Security Architect

Tips to get a job in top companies - Find out about the strategy and preparation to get started with Cybersecurity
As companies adopt cloud services, IoT devices, and remote work solutions, their attack surface expands. Cybersecurity experts are essential to ensure the security of these technologies and networks. The expertise of cybersecurity specialists bolster
Latest blogs on technology to explore

Cyber Security in 2025: The Golden Ticket to a Future-Proof Career
Cyber security jobs are growing 35% faster than any other tech field (U.S. Bureau of Labor Statistics, 2024)—and the average salary is $100,000+ per year! In a world where data breaches cost businesses $4.45 million on average (IBM, 2024), cyber secu

SAP SD in 2025: Your Ticket to a High-Flying IT Career
In the fast-paced world of IT and enterprise software, SAP SD (Sales and Distribution) is the secret sauce that keeps businesses running smoothly. Whether it’s managing customer orders, pricing, shipping, or billing, SAP SD is the backbone of sales o

SAP FICO in 2025: Salary, Jobs & How to Get Certified
AP FICO professionals earn $90,000–$130,000/year in the USA and Canada—and demand is skyrocketing! If you’re eyeing a future-proof IT career, SAP FICO (Financial Accounting & Controlling) is your golden ticket. But where do you start? Sulekha IT Serv

Train Like an AI Engineer: The Smartest Career Move You’ll Make This Year!
Why AI Engineering Is the Hottest Skillset Right Now From self-driving cars to chatbots that sound eerily human, Artificial Intelligence is no longer science fiction — it’s the backbone of modern tech. And guess what? Companies across the USA and Can
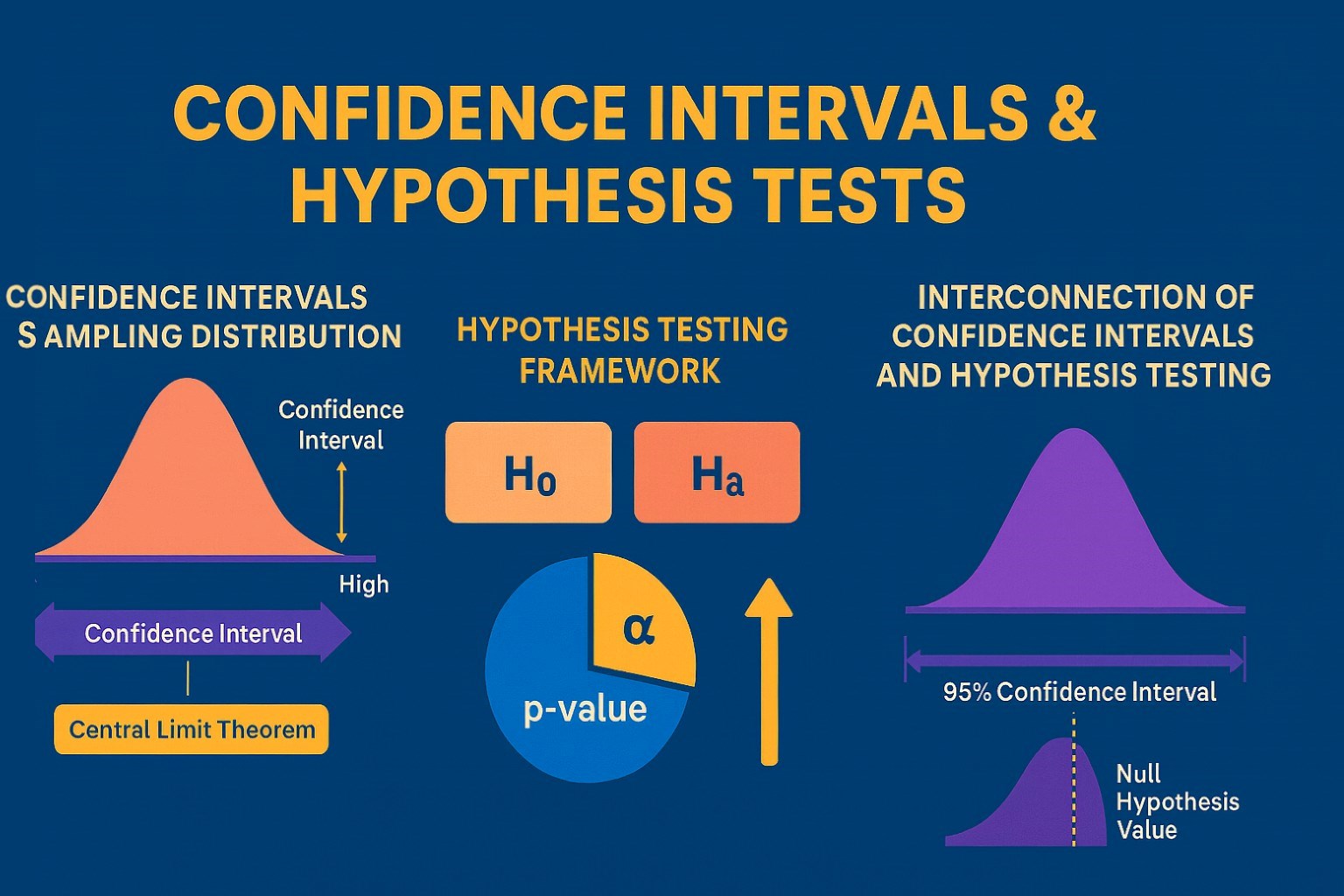
Confidence Intervals & Hypothesis Tests: The Data Science Path to Generalization
Learn how confidence intervals and hypothesis tests turn sample data into reliable population insights in data science. Understand CLT, p-values, and significance to generalize results, quantify uncertainty, and make evidence-based decisions.

What Is a Security Classification Guide in Cybersecurity?
A Security Classification Guide (SCG) defines how to categorize information assets by sensitivity, with clear instructions from authorized officials to ensure consistent, compliant data handling.
Artificial Intelligence – Field of Study
Explore how Artificial Intelligence blends Machine Learning, Deep Learning, NLP, and Computer Vision to build intelligent systems that learn, reason, and decide. Discover real world applications, ethics, and booming career scope as AI education deman

Understanding Artificial Intelligence: Hype, Reality, and the Road Ahead
Explore the reality of Artificial Intelligence (AI) — its impact, how it works, and its potential risks. Understand AI's benefits, challenges, and how to navigate its role in shaping industries and everyday life with expert training programs

How Much Do Healthcare Administrators Make?
Discover how much healthcare administrators make, the importance of healthcare, career opportunities, and potential job roles. Learn about salary ranges, career growth, and training programs with Sulekha to kickstart your healthcare administration jo

How to Gain the High-Income Skills Employers Are Looking For?
Discover top high-income skills like software development, data analysis, AI, and project management that employers seek. Learn key skills and growth opportunities to boost your career.
