What Are Most Sought-After Certifications For Ethical Hackers?
One of the high demand jobs in the IT field is that of an ethical hacker, who intentionally penetrates into the systems and networks to detect and fix vulnerabilities.The term hacking of computers, carries with it a negative impact. It just brings to the mind images of techies stealing customer identities, sensitive information and disabling vital computer networks but hacking can also be used to bring about positive results and this is known as ethical hacking or intrusion testing, red teaming, or penetration testing.
By this act professional hackers or ethical hackers determine the vulnerabilities and weaknesses of information or computer systems of an organization by the techniques adopted by the malicious hackers. As a result, you could land a high caliber job by doing one of the most sought after certification courses in ethical hacking.
The Responsibilities of an Ethical Hacker Are:
- They have the responsibility of offering recommendations on how to reduce vulnerabilities.
- They work with developers to advice on the security requirements.
- They have the responsibility of updating procedures and security policies.
- They also provide the training as part of the training program and an organization’s security awareness.
Requirements to Get the Job ofan Ethical Hacker:
For an entry level ethical hacker a Bachelor’s degree in Computer Science or associated field is absolutely necessary. Beyond this level of education, security certifications are necessary.
The Most Sought-After Certifications For Ethical Hackers Are:

#1.CEH: The Most Basic and Widely Recognized Certification
The most basic certification to start the career as an Ethical hacker is CEH. It is provided by the EC-Council and is designed in a way to offer the IT security professionals a general knowledge of countermeasures, risks, knowledge of the security threats through the hands-on labs and lectures. Students who enroll for this course should have adequate knowledge of the Linux and Windows systems administration skills and should be familiar with virtualization and the TCP/IP (Core Internet Protocol).
Skills Learnt From The Course:
- The course covers how to identify the basic viruses to hijacking web servers, scan networks and penetration testing.
- It teaches how to crack the passwords, hack wireless networks, remote access Trojans and perform the denial of service (DoS) attacks.
- It gives an understanding of social engineering or the procedure of manipulating the individuals to obtain personal information. Social engineering is crucial to stay ahead of the threats.
- The course concentrates on RAPID 7, which is a suite of tools that helps the ethical hackers in the comprehensive pen tests including planning, scanning and final analysis.
Benefits Offered By This Certification:
This certification is highly recognized of the three certifications. It raises the pay scale. A CEH-certified professional earns 8.9% more than the non-certified professionals
#2.GPEN: A More Comprehensive, yet Costly Certification
This certification is needed to learn ethical hacking in depth. Prior to taking this course, students should have adequate knowledge of Linux, Windows, and TCP/IP.
Skills Learnt From The Course:
- It teaches how to learn penetration tests that have high business value.
- The main goal of this course is to make a candidate ready to do comprehensive pentests.
- It teaches the IT professionals how to think from the point of view of a hacker.
Benefits Offered By This Certification:
This course is a good balance between hands-on experience and theory. It provides a good job in developing the soft skills required to be successful as an ethical hacker.
#3.OSCP: The Lesser-Known, More Technical Certification
This is a technical certification and it is for the students to prove that they have a practical and a clear understanding of penetration testing process and the lifecycle.
Skills Learnt From The Course:
- It teaches how to take a creative approach to solve problems.
- Apart from learning about the pen testing techniques and tools, it teaches how to think laterally.
Benefits Offered By This Certification:
It offers the best hands-on experience as offensive security needs to be learnt in the legal environment with real scenarios and tools. The skill learnt from this certification course is more valuable than the certification itself.
The job of a white hat or ethical hacker is of high demand in the IT industry and you could make the right career move by earning a certified ethical hacker certification.
Find a course provider to learn Ethical Hacking
Java training | J2EE training | J2EE Jboss training | Apache JMeter trainingTake the next step towards your professional goals in Ethical Hacking
Don't hesitate to talk with our course advisor right now
Receive a call
Contact NowMake a call
+1-732-338-7323Enroll for the next batch
Certified Ethical Hacker Course
- Dec 8 2025
- Online
Certified Ethical Hacker Course
- Dec 9 2025
- Online
Certified Ethical Hacker Course
- Dec 10 2025
- Online
Related blogs on Ethical Hacking to learn more

Top 15 Ethical Hacking Tools to Use in 2024
In top 20 Ethical Hacking Tools and Software, we have discussed What is Ethical hacking, what are Ethical Hacking Tools and Software and the importance of Hacking Tools.

What are the Advantages of Ethical Hacking?
Ethical hacking is a proliferating career path among various rapidly evolving technologies in the IT and non-IT industries.

A glance into the world of Ethical hacking
A hacker is an individual or a group of people who steals the private information of a person or an organization and gains advantages from it from their digital device or network using various hacking tools. Majorly there are three types of hackers:

How to Boost Cyber Security As An Ethical Hacker
Cyber security is protecting the Information systems from damage or theft of the software, hardware and to the sensitive information on them. It involves the controlling of the access to the hardware and protecting

The Importance of Penetration Testing and What it takes to be a Penetration Tester
“What is penetration testing?” is a commonly asked question. Penetration testing is a complex process that involves testing applications for security vulnerabilities. Easier said than done, penetration testing has become a major part of ethical hacki

A Comprehensive Guide To Become A Successful White Hat Hacker
Hacking is considered to be an offense but it is ethical, when under a contract between an organization and a hacker. Breaking into the computer system was a practice of the geeks but now surprisingly, it is a career option. In the past few years, th

Ethical Hacking – Offering Several Advantages
The term ‘hacking of computers’; carries with it a negative impact. It just brings to the mind images of techies stealing customer identities, sensitive information and disabling vital computer networks but hacking can also be used to bring about pos
Latest blogs on technology to explore

From Student to AI Pro: What Does Prompt Engineering Entail and How Do You Start?
Explore the growing field of prompt engineering, a vital skill for AI enthusiasts. Learn how to craft optimized prompts for tools like ChatGPT and Gemini, and discover the career opportunities and skills needed to succeed in this fast-evolving indust

How Security Classification Guides Strengthen Data Protection in Modern Cybersecurity
A Security Classification Guide (SCG) defines data protection standards, ensuring sensitive information is handled securely across all levels. By outlining confidentiality, access controls, and declassification procedures, SCGs strengthen cybersecuri

Artificial Intelligence – A Growing Field of Study for Modern Learners
Artificial Intelligence is becoming a top study choice due to high job demand and future scope. This blog explains key subjects, career opportunities, and a simple AI study roadmap to help beginners start learning and build a strong career in the AI

Java in 2026: Why This ‘Old’ Language Is Still Your Golden Ticket to a Tech Career (And Where to Learn It!
Think Java is old news? Think again! 90% of Fortune 500 companies (yes, including Google, Amazon, and Netflix) run on Java (Oracle, 2025). From Android apps to banking systems, Java is the backbone of tech—and Sulekha IT Services is your fast track t
From Student to AI Pro: What Does Prompt Engineering Entail and How Do You Start?
Learn what prompt engineering is, why it matters, and how students and professionals can start mastering AI tools like ChatGPT, Gemini, and Copilot.

Cyber Security in 2025: The Golden Ticket to a Future-Proof Career
Cyber security jobs are growing 35% faster than any other tech field (U.S. Bureau of Labor Statistics, 2024)—and the average salary is $100,000+ per year! In a world where data breaches cost businesses $4.45 million on average (IBM, 2024), cyber secu

SAP SD in 2025: Your Ticket to a High-Flying IT Career
In the fast-paced world of IT and enterprise software, SAP SD (Sales and Distribution) is the secret sauce that keeps businesses running smoothly. Whether it’s managing customer orders, pricing, shipping, or billing, SAP SD is the backbone of sales o

SAP FICO in 2025: Salary, Jobs & How to Get Certified
AP FICO professionals earn $90,000–$130,000/year in the USA and Canada—and demand is skyrocketing! If you’re eyeing a future-proof IT career, SAP FICO (Financial Accounting & Controlling) is your golden ticket. But where do you start? Sulekha IT Serv

Train Like an AI Engineer: The Smartest Career Move You’ll Make This Year!
Why AI Engineering Is the Hottest Skillset Right Now From self-driving cars to chatbots that sound eerily human, Artificial Intelligence is no longer science fiction — it’s the backbone of modern tech. And guess what? Companies across the USA and Can
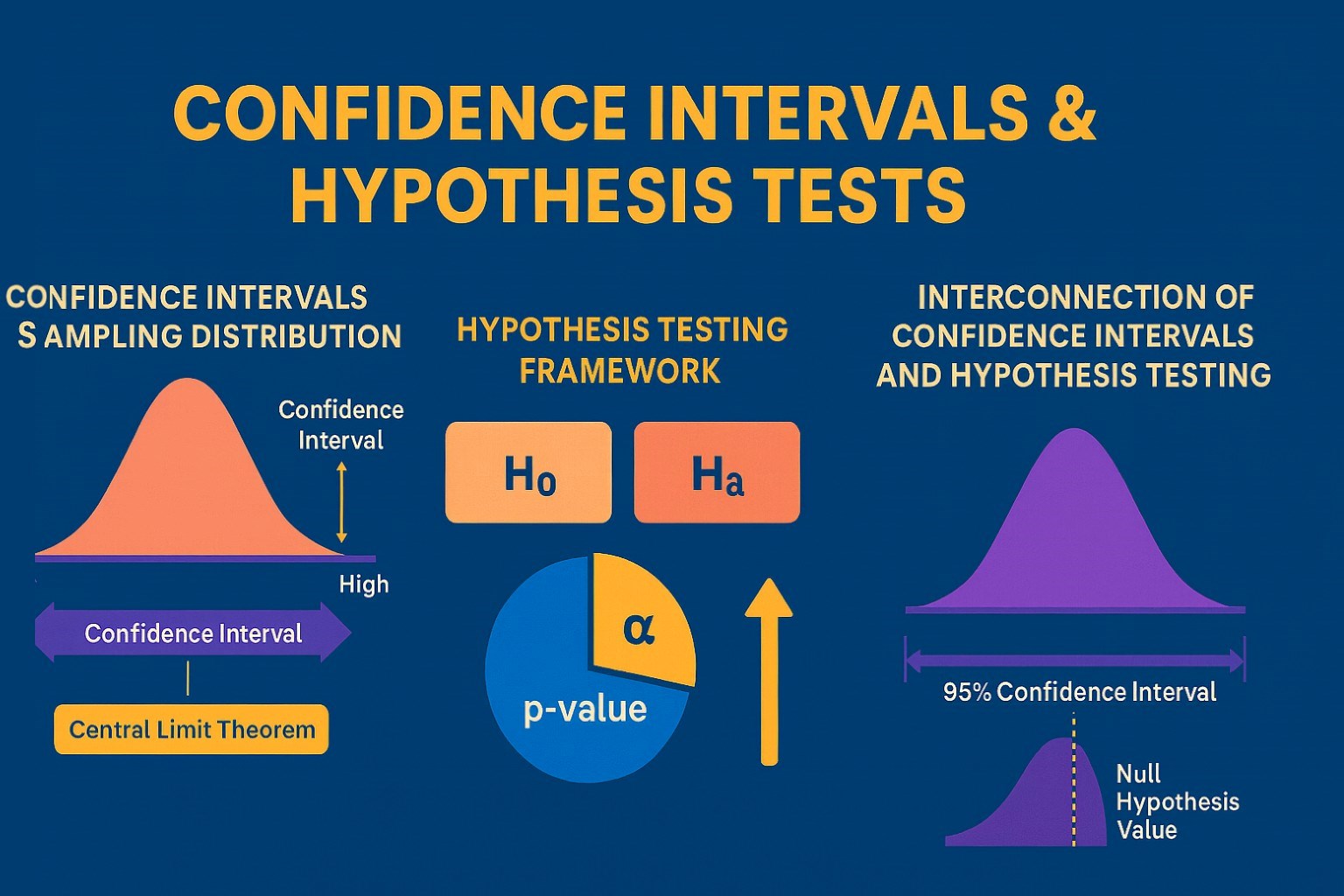
Confidence Intervals & Hypothesis Tests: The Data Science Path to Generalization
Learn how confidence intervals and hypothesis tests turn sample data into reliable population insights in data science. Understand CLT, p-values, and significance to generalize results, quantify uncertainty, and make evidence-based decisions.