A glance into the world of Ethical hacking

A hacker is an individual or a group of people who steals the private information of a person or an organization and gains advantages from it from their digital device or network using various hacking tools.
Majorly there are three types of hackers:
1. White hat Hacker (Ethical Hacker)
2. Black hat Hacker (Cracker)
3. Grey hat Hacker
White hat hacker: The hacker who accesses your system to fix the identifiable errors and weaknesses. This type of hacking is also called as ethical hacking, and it legalized in the industry. They are used to perform Testing and vulnerability assessments.
Black hat hacker: A hacker who takes advantage over your system for personal benefits, he violates the policies of ethical hacking by unauthorized access to computer systems. Most of the time the intention is to steal corporate data, violate privacy rights, transfer funds from bank accounts and to trap an individual. A black hat hacker is also known as Cracker.
Grey hat hacker: A hacker who lies somewhere between the grey areas of good and bad, i.e white hat hacking and black hat hacking is known as a grey hat hacker. He enters through an unauthorized way to get access to your system. He finds errors in the data and reveals it to the system owner.
Apart from the above hackers, there are three other minor types of hackers
Elite Hackers, Script Kiddie, and Neophyte.
Types of Ethical Hacking:
These are the common and most happening types of ethical hacking
1. Web application hacking
2. System hacking
3. Web server hacking
4. Hacking wireless network and
5. Social network hacking.
6. Web application hacking: hacking and entering the website with unauthorized access is known as Web application hacking
Ex: SQL Injection attacks.
1. System hacking: violating the policies, principles and hacking the system to get personal information or corporate information is system hacking.
2. Web server hacking: Attacking the web server network to claim data’s is web server hacking
3. Hacking wireless network: Using devices to hack a wireless network is wireless network hacking
4. Social network hacking: in the era of social networking, hacking social networking platforms of personals for personal gains or defaming is social network hacking.
Process of Ethical Hacking:
Ethical hacking falls under the following steps:
- Planning
- Scanning
- Accessing
- Retrieving
- Analyzing
Ethical hacking has been here in many MNC’s and government sectors to prevent data stealing, students and professionals are showing interest in ethical hacking courses for a long run in their career. To learn ethical hacking visit the following webpage at Sulekha it training
Find a course provider to learn Ethical Hacking
Java training | J2EE training | J2EE Jboss training | Apache JMeter trainingTake the next step towards your professional goals in Ethical Hacking
Don't hesitate to talk with our course advisor right now
Receive a call
Contact NowMake a call
+1-732-338-7323Enroll for the next batch
Ethical Hacking Certification Training Course Program
- Nov 5 2025
- Online
Related blogs on Ethical Hacking to learn more

Top 15 Ethical Hacking Tools to Use in 2024
In top 20 Ethical Hacking Tools and Software, we have discussed What is Ethical hacking, what are Ethical Hacking Tools and Software and the importance of Hacking Tools.

What are the Advantages of Ethical Hacking?
Ethical hacking is a proliferating career path among various rapidly evolving technologies in the IT and non-IT industries.

How to Boost Cyber Security As An Ethical Hacker
Cyber security is protecting the Information systems from damage or theft of the software, hardware and to the sensitive information on them. It involves the controlling of the access to the hardware and protecting

What Are Most Sought-After Certifications For Ethical Hackers?
One of the high demand jobs in the IT field is that of an ethical hacker, who intentionally penetrates into the systems and networks to detect and fix vulnerabilities.The term hacking of computers, carries with it a negative impact. It just brings to

The Importance of Penetration Testing and What it takes to be a Penetration Tester
“What is penetration testing?” is a commonly asked question. Penetration testing is a complex process that involves testing applications for security vulnerabilities. Easier said than done, penetration testing has become a major part of ethical hacki

A Comprehensive Guide To Become A Successful White Hat Hacker
Hacking is considered to be an offense but it is ethical, when under a contract between an organization and a hacker. Breaking into the computer system was a practice of the geeks but now surprisingly, it is a career option. In the past few years, th

Ethical Hacking – Offering Several Advantages
The term ‘hacking of computers’; carries with it a negative impact. It just brings to the mind images of techies stealing customer identities, sensitive information and disabling vital computer networks but hacking can also be used to bring about pos
Latest blogs on technology to explore

Cyber Security in 2025: The Golden Ticket to a Future-Proof Career
Cyber security jobs are growing 35% faster than any other tech field (U.S. Bureau of Labor Statistics, 2024)—and the average salary is $100,000+ per year! In a world where data breaches cost businesses $4.45 million on average (IBM, 2024), cyber secu

SAP SD in 2025: Your Ticket to a High-Flying IT Career
In the fast-paced world of IT and enterprise software, SAP SD (Sales and Distribution) is the secret sauce that keeps businesses running smoothly. Whether it’s managing customer orders, pricing, shipping, or billing, SAP SD is the backbone of sales o

SAP FICO in 2025: Salary, Jobs & How to Get Certified
AP FICO professionals earn $90,000–$130,000/year in the USA and Canada—and demand is skyrocketing! If you’re eyeing a future-proof IT career, SAP FICO (Financial Accounting & Controlling) is your golden ticket. But where do you start? Sulekha IT Serv

Train Like an AI Engineer: The Smartest Career Move You’ll Make This Year!
Why AI Engineering Is the Hottest Skillset Right Now From self-driving cars to chatbots that sound eerily human, Artificial Intelligence is no longer science fiction — it’s the backbone of modern tech. And guess what? Companies across the USA and Can
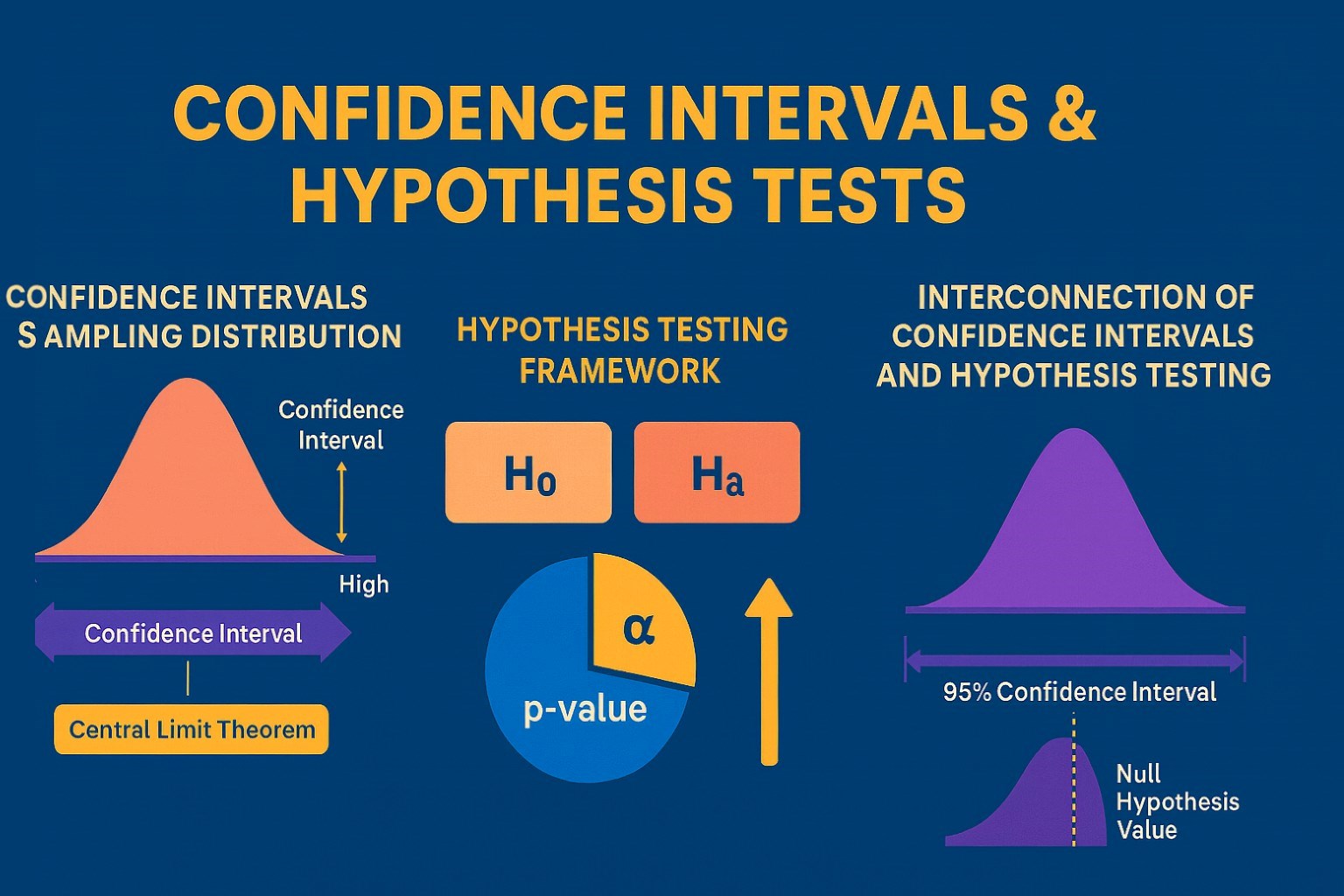
Confidence Intervals & Hypothesis Tests: The Data Science Path to Generalization
Learn how confidence intervals and hypothesis tests turn sample data into reliable population insights in data science. Understand CLT, p-values, and significance to generalize results, quantify uncertainty, and make evidence-based decisions.

What Is a Security Classification Guide in Cybersecurity?
A Security Classification Guide (SCG) defines how to categorize information assets by sensitivity, with clear instructions from authorized officials to ensure consistent, compliant data handling.
Artificial Intelligence – Field of Study
Explore how Artificial Intelligence blends Machine Learning, Deep Learning, NLP, and Computer Vision to build intelligent systems that learn, reason, and decide. Discover real world applications, ethics, and booming career scope as AI education deman

Understanding Artificial Intelligence: Hype, Reality, and the Road Ahead
Explore the reality of Artificial Intelligence (AI) — its impact, how it works, and its potential risks. Understand AI's benefits, challenges, and how to navigate its role in shaping industries and everyday life with expert training programs

How Much Do Healthcare Administrators Make?
Discover how much healthcare administrators make, the importance of healthcare, career opportunities, and potential job roles. Learn about salary ranges, career growth, and training programs with Sulekha to kickstart your healthcare administration jo

How to Gain the High-Income Skills Employers Are Looking For?
Discover top high-income skills like software development, data analysis, AI, and project management that employers seek. Learn key skills and growth opportunities to boost your career.