
CCENT Certification
The Cisco CCENT (Cisco Certified Entry Networking Technician Certification) will help you to gain the fundamentals of computer networking. This is your first baby step into the world of networking and a foundational course for advanced Cisco certifications. Certification in networking is a tangible method to demonstrate your skills and knowledge in the networking domain. The certification is given by Cisco to add a feather in your cap.
Benefits of CCENT Certification
A CCENT certification will help you to gain knowledge of the functions and operations of various network devices. You will learn to implement switched networks and configure IP services for a small branch office. You will learn to identify security threats and mitigate them. This certification will help you to connect, configure, and verify the operational status of the network devise interface. You just need to pass one test to travel on the longer Cisco certifications path.
Benefits to Career
A certification in CCENT is a boost to your career and opens doors into the networking domain. A certification from Cisco will value add to your CV and will give you visibility before the employers to hire you. You will have the edge over your peers to get employed. You can start your career as a network engineer, network administrator, system administrator, network technician, system administrator, etc. Popular companies like Amazon, Cisco, SAIC, General dynamics information technology, etc. will hire you for a suitable position in networking. The average salary is $60 k for a network technician. If you decide to work as a freelancer, then you may be paid up to $25 per hour. The salary range can be from 31,000 - $93,000 per year.
-------------------------------------------------------------------------------------------------------------------------------
Best CCENT Exam Questions to practice for CCENT Certification Exam
A CCENT certification is the first step to enter into the gamut of Cisco certifications. With this certification, you will be efficient to handle a small office branch network. The CCENT certification is a baby step to walk towards the associate certifications like CCNA. To clear this CCENT certification exam, you should have networking fundamentals knowledge, knowledge of WAN technologies, security and basic wireless concepts, fundamentals of routing, and switching. There are no prerequisites to take CCENT certification exam. However, knowledge of networking protocols is desired. We are here to take the first step in the Cisco certifications world. We have a bunch of compiled CCENT practice test questions and answers, which will help you to recap before taking the CCENT test. You can use them as CCENT practice exam or glance to brush your memory. All the CCENT dumps have a correct answer with an explanation to correct the solution. Use or intellectual property and step into the fantastic world of networking.
The objective of these CCENT sample questions for practicing and to give you confidence for passing score. Use these sample questions and answers as a free ccent practice test to check your knowledge on the subject and how you handle to complete it on the given exam duration.
Exam details: Cisco Certified Entry Networking Technician
Exam name: CCENT
Duration: 90 minutes
No. of questions: 50-60
Passing score: 75%
Validated against: CISCO
Format: Multiple choice questions
Exam price: $125
--------------------------------------------------------------------------------------------------------------------------------
1. From the below-mentioned option which command will help us to achieve the below-mentioned target?
Our target is of assigning port 3 of our catalyst 2950 switch with VLAN 3.
A. switch#switchport access VLAN 3
B. switch(config)#switchport access VLAN 3
- switch(config-if)#switchport access VLAN 3
D. switch(config-if)#switchport VLAN 3
Explanation- configuration to a switch port to VLAN is commanded by the switch port access VLAN (number). Another option using the switch port access VLAN dynamically by command for configuring the switch port automatically in a certain VLAN that depends upon the membership of the VLAN of incoming packets. The switch port is required to be in access mode for the proper working of both the command.
-----------------------------------------------------------------------------------------------------------------------------
2. From the below-mentioned option which command is used for providing the permission to SSH for connecting with the router?
A. Transport SSH
B. Transport input telnet SSH
C. Transport input SSH
D. Transport SSH enable.
Explanation- the transport input SSH line configuration commands is the only correct option among the four options mentioned above. It is the only command that is used for creating a connection only to the router.
--------------------------------------------------------------------------------------------------------------------------------------------------------
3. Mention whether the following statement is true or false?
Transport SSH enables command is used for creating a connection of SSH to the router
A. True
B. False
C. Partly true and partly false
D. None of the above
Explanation- the transport input SSH is the only command that is used for creating a connection only to the router. Since transport SSH enables is not used for connecting to the router, hence the above statement is false.
-----------------------------------------------------------------------------------------------------------------------------------------------------
4. From the below-mentioned option which utility is used for testing an all 7 layers of OSI?
A. Ping
B. Telnet
C. Traceroute
D. Show ARP
Explanation- if telnet is done easily from one device to other it is the proof that the routing layer 3 and the physical layer working is going on nicely. Telnet is also called as application layer utility. Hence it provides us the confirmation about the working of all 7 OSI layers between 2 devices.
--------------------------------------------------------------------------------------------------------------------------------------------------------
5. There is a task provided by Mr. XYZ who is the network administrator of the global company. He is asked for the future expansion of the network. Mr. XYZ decided that he will subnet the current network of 172.15.0. If each subnet allocates 500 hosts from the below-mentioned option which will be the correct option for subnet marks.
A. 255.255.254.0
- 255.0.0.0
C. 255.255.0.0
D. 255.255.240.0
Explanation- as it is required that each subnet must allocate 500 hosts the calculation will be achieved by the following: 2^9 = 512. Hence by deducting the broadcast and network address the total number of possible hosts is 510. For allocating the host we use 9 bits and from these 9 bits, 7 bits are left for possible subnets. The binary for the 7 bits is 1111 1110 and the decimal for 7 bits is 254.
--------------------------------------------------------------------------------------------------------------------------------------------------------
6. From the below-mentioned option which of the following address range is used for testing purposes?
A. 10.0.0.0/16
B. 240.0.0.0 – 255.255.255.255
C. 127.0.0.0/8
D. Any available IP Address
Explanation- 127.0.0.0/8 is the address range used for testing purposes. In class A range which is a reserved address range.
-------------------------------------------------------------------------------------------------------------------------------------------------------
7. From the below-mentioned option which router is available for the following situation?
We have multiple iOS versions on our router.
A. Show memory
B. Show version
C. Show file system
D. Show flash
Explanation- the show flash command is used for displaying the content in a flash file system.
----------------------------------------------------------------------------------------------------------------------------------------------------
8. From the below-mentioned option which of the following is used for displaying a message in terminals which is connected with the router?
A. Banner slip-PPP
B. Banner motd
C. Banner logging
D. Banner exec
Explanation- the motd banner is the banner used for displaying a message for all the terminals which is connected by routers. It is used for sending a message which affects all the users. For example, the impending system shuts down. For disabling the MOTD banner on a line the commands used are no exec- banner or no motd- banner. For disabling the exec banner on the line the command used is no exec-banner. Before the login from the MOTD banner is appeared after the user connects to the router. When the user login to the router there will be a display of incoming banner or exec banner. This will be based on the connection type. While the incoming banner will display if reverse telnet is log in. And for the remaining connection exec banner will be displayed.
--------------------------------------------------------------------------------------------------------------------------------
9. From the below-mentioned option which is included invalid options of court security?
A. Restrict
B. Protect
C. Shut down
D. All of the above
Explanation- shut down, protect and restrict are the options available in the switch port security, port-security violation interface configuration command. Hence the correct option is D.
-------------------------------------------------------------------------------------------------------------------------------------------------------
10. From the below-mentioned option what are the reasons included in and responsible for the implementation of VLANs by network administrator?
A. Security
B. Broadcast control
C. Enhancement of performance
D. All of the above.
Explanation- some reasons lead to the implementation of VLANs by the network administrator. Some of the common reasons are Security, Project application, Band with or performance, Traffic flow or broadcast, Specific job type or departments
------------------------------------------------------------------------------------------------------------------------------------------------------
11. Form the below-mentioned option which statement matches the best and describes full-duplex Ethernet?
A. Full duplex Ethernet has a very low speed which is limited to up to 100 MB.
B. Point to point connection is used in full-duplex Ethernet.
C. Ethernet uses point to multi point connection.
D. All of the above.
Explanation- point to point connection is used by a full-duplex Ethernet between the switch and the device. Hence the correct option is B.
-------------------------------------------------------------------------------------------------------------------------------------------------------
12. From the below-mentioned option, what is the best choice for transferring the data securely on the internet?
A. VPN
B. URL filtering
C. Leased line
D. Anti- X
Explanation- the best thing used for transferring data across the insecure media is VPN. One of the examples of VPN is the internet. Hence the correct option is A.
--------------------------------------------------------------------------------------------------------------------------------------------------------
13. --- is the address field found in a frame relay header.
A. PVC
B. MAC
C. DLCI
D. SVC
Explanation- for addressing the field in frame relay order data-link connection identifier is used. (DLCI). Hence the correct option is C.
--------------------------------------------------------------------------------------------------------------------------------------------------------
14. From the below-mentioned option which of the following protocol is called a routing protocol?
A. Border gateway protocol (BGP)
B. Open shortest path first (OSPF)
C. Enhance interior gateway routing protocol (ENHANCED IGRP)
D. All of the above
Explanation- routing protocol is used for the intermediate system for building tables using it for the determination of path selection of router and protocol. Border gateway protocol (BGP), Open shortest path first (OSPF), Enhance interior gateway routing protocol (ENHANCED IGRP) are included or examples of these protocols. Hence the correct option is D.
--------------------------------------------------------------------------------------------------------------------------------------------------------
15. Mention whether the following statement is true or false?
Exterior gateway protocol and intermediate system to intermediate system (IS - IS) are the examples of routing protocol which is used for an intermediate system for building tables using it for determination of path selection of router and protocol.
A. True
B. False
C. Partly true and partly false
D. None of the above
Explanation- Routing protocol is used for the intermediate system for building tables using it for the determination of path selection of router and protocol. Border gateway protocol (BGP), Open shortest path first (OSPF), Enhance interior gateway routing protocol (ENHANCED IGRP), intermediate system to intermediate system (IS - IS) and gateway protocol are included or example of these protocols. Hence the correct option is A.
--------------------------------------------------------------------------------------------------------------------------------
16. From the below-mentioned option which of the protocol is called a routing protocol?
A. FTP
B. SMTP
C. SNMP
D. IGRP
Explanation- routing protocol is used for the intermediate system for building tables using it for the determination of path selection of router and protocol. Border gateway protocol (BGP), Open shortest path first (OSPF), Enhance interior gateway routing protocol (ENHANCED IGRP), intermediate system to intermediate system (IS - IS) and gateway protocol are included or example of these protocols. FTP, SMTP, and SNMP are not included as routing protocol. Hence the correct option is A.
--------------------------------------------------------------------------------------------------------------------------------------------------------
17. For the below-mentioned statement which protocol must be used from the below-mentioned option?
Mr. Shubham a network administrator of the local company wants that he can make assigning of IP address to host as a very easy process.
A. DHCP
B. DNS
C. NTP
D. HSRP
Explanation- for making it easy to assign the IP addresses to host the protocol that can be used is DHCP. DHCP is the protocol described by RFC-1541 or dynamic host configuration protocol which is used for assessment network addresses and host-specific configuration parameters.
--------------------------------------------------------------------------------------------------------------------------------------------------------
18. Which of the following command is used for finding the time of the router in online mode?
A. Show hardware
B. Show uptime
C. Show history
D. Show version
E. All of the above
Explanation- for finding out how long the router was online the command that we use is show version.
--------------------------------------------------------------------------------------------------------------------------------------------------------
19. From the below-mentioned option which of the command is used for changing the hostname of the router?
A. router#host name new name
B. router(config)#hostname new name
C. router(config-router)#hostname new name
D. router>host name new name
Explanation- for modifying the hostname of the router or changing it or to specify it in the network server the hostname used is a router(config)#hostname new name. Hence the correct option is B.
--------------------------------------------------------------------------------------------------------------------------------------------------------
20. From the below-mentioned option which of the following is found in the Cisco router serial interface as a default Incapsulation?
A. SDLC
B. PPP
C. frame relay
D. HDLC
Explanation- high-level data link control is used as the default encapsulation on a Cisco router serial interface. High-level data link control, Bit orientated synchronous data link layer protocol which is developed by ISO. HDLC is derived from SDLC. It has a specific data encapsulation method on synchronizing serial links by using frame characters and checksums. Hence the correct option is D.
--------------------------------------------------------------------------------------------------------------------------------------------------------
21. Form the below-mentioned option which of the following routing protocol are included in the interior protocol?
A. Open shorted path first. (OSPF)
B. Intermediate system to intermediate system (IS - IS)
C. Enhanced internet gateway routing protocol (Enhanced IGRP)
D. All of the above.
Explanation- interior protocol is the routing protocol that is used for routing networks that come under the common network administration. Interior protocol must be provided with a specification that lists of associated networks before performing or beginning of any routine activity. Cisco iOS software supports the below-mentioned interior routing protocols. Internet Gateway Routing Protocol (IGRP), Routing Information Protocol (RIP), Intermediate System-to-Intermediate System (IS-IS), Open Shortest Path First (OSPF), Enhanced Internet Gateway Routing Protocol (Enhanced IGRP). Hence the above 3 options are examples of the interior protocol.
--------------------------------------------------------------------------------------------------------------------------------------------------------
22. Internet gateway protocol and BGP are examples of the interior protocol used for routing networks under a common network administration. Mention whether the following statement is true or false.
A. True
B. False
C. Partly true and partly false
D. None of the above
Explanation- interior protocol is the routing protocol that is used for routing networks that comes under the common network administration. Interior protocol must be provided with a specification that lists of associated networks before performing or beginning of any routine activity. Cisco iOS software supports the below mentioned interior routine protocols. Internet Gateway Routing Protocol (IGRP), Routing Information Protocol (RIP), Intermediate System-to-Intermediate System (IS-IS), Open Shortest Path First (OSPF), Enhanced Internet Gateway Routing Protocol (Enhanced IGRP). Hence the above 3 options are examples of the interior protocol. Since BGP IS not the interior routing protocol the statement is partly false and IGR is the routing protocol hence the statement is partly true.
--------------------------------------------------------------------------------------------------------------------------------------------------------
23. From the below-mentioned option, what is the advantage of the OSI model's layer?
A. Modifications in one layer do not affect the other layer.
B. It helps in preventing routing loops.
C. Whatever the changes in done in one layer it gets propagate in other layers too.
D. The networks are hard to design.
E. All of the above
Explanation- there are various advantages of having the layers in the OSI model. Some of them are, Modifications in one layer do not affect the other layer, It helps with making the networks extensible, It helps with creating a connection between various hardware and software, It allows interoperation for different vendor's networks.
-------------------------------------------------------------------------------------------------------------------------------------------------------
24. Which of the following key sequence is used for moving the cursor at the initiation point of any line?
A. Control+E
B. Control+A
C. Control+F
D. Control+P
Explanation- control+E is used for taking the cursor at the end of the command line. Control+P is used for recalling the commands in the history buffer which starts with the recently used command. Control+F is used for moving the cursor one-character forward. The only control+A is used for moving the cursor at the starting point of any command line. Hence the correct option is A.
--------------------------------------------------------------------------------------------------------------------------------------------------------
25. From the below-mentioned option which of the following is the incorrect match?
A. control+E is used for taking the cursor at the end of the command line.
B. Control+P is used for recalling the commands in the history buffer which starts with the recently used command.
C. Control+F is used for moving the cursor one character forward.
D. control+A Is used for moving the cursor at the starting point of any command line.
E. Control+B is used for moving the cursor one character forward.
Explanation- control+E is used for taking the cursor at the end of the command line. Control+P is used for recalling the commands in the history buffer which starts with the recently used command. Control+F is used for moving the cursor one character forward. The only control+A is used for moving the cursor at the starting point of any command line. Control+B is used for moving the cursor one character back. Hence the correct option is E.
--------------------------------------------------------------------------------------------------------------------------------------------------------
26. From the below-mentioned option which kind of attack is used for the collection of information?
A. DOS attack
B. Access attack
C. DDOS attack
D. Reconnaissance attack
Explanation- for collecting the information the attack used is reconnaissance attack and the information is used for the preparation of the further attack. Hence the correct option is D.
--------------------------------------------------------------------------------------------------------------------------------------------------------
27. Which command is used for the below-mentioned situation?
Our router has restarted and we are searching for the reasons behind it.
A. Show history
B. Show IP protocol
C. Show version
D. Show startup-config
Explanation- whenever we issue the show version command, the output displays a line mentioning that "system restarted by" and it contains the reason and from for the cause of restarting of the router.
--------------------------------------------------------------------------------------------------------------------------------------------------------
28. How many numbers of bytes are required for making up with the network portion of the classy address?
A. 1
B. 2
C. 4
D. 3
Explanation- the size of an octet is 1 byte long and for the representation of the network part the 1 three octets of class C addresses it.
Find a course provider to learn CCENT
Java training | J2EE training | J2EE Jboss training | Apache JMeter trainingTake the next step towards your professional goals in CCENT
Don't hesitate to talk with our course advisor right now
Receive a call
Contact NowMake a call
+1-732-338-7323Enroll for the next batch
Latest blogs on technology to explore

From Student to AI Pro: What Does Prompt Engineering Entail and How Do You Start?
Explore the growing field of prompt engineering, a vital skill for AI enthusiasts. Learn how to craft optimized prompts for tools like ChatGPT and Gemini, and discover the career opportunities and skills needed to succeed in this fast-evolving indust

How Security Classification Guides Strengthen Data Protection in Modern Cybersecurity
A Security Classification Guide (SCG) defines data protection standards, ensuring sensitive information is handled securely across all levels. By outlining confidentiality, access controls, and declassification procedures, SCGs strengthen cybersecuri

Artificial Intelligence – A Growing Field of Study for Modern Learners
Artificial Intelligence is becoming a top study choice due to high job demand and future scope. This blog explains key subjects, career opportunities, and a simple AI study roadmap to help beginners start learning and build a strong career in the AI

Java in 2026: Why This ‘Old’ Language Is Still Your Golden Ticket to a Tech Career (And Where to Learn It!
Think Java is old news? Think again! 90% of Fortune 500 companies (yes, including Google, Amazon, and Netflix) run on Java (Oracle, 2025). From Android apps to banking systems, Java is the backbone of tech—and Sulekha IT Services is your fast track t
From Student to AI Pro: What Does Prompt Engineering Entail and How Do You Start?
Learn what prompt engineering is, why it matters, and how students and professionals can start mastering AI tools like ChatGPT, Gemini, and Copilot.

Cyber Security in 2025: The Golden Ticket to a Future-Proof Career
Cyber security jobs are growing 35% faster than any other tech field (U.S. Bureau of Labor Statistics, 2024)—and the average salary is $100,000+ per year! In a world where data breaches cost businesses $4.45 million on average (IBM, 2024), cyber secu

SAP SD in 2025: Your Ticket to a High-Flying IT Career
In the fast-paced world of IT and enterprise software, SAP SD (Sales and Distribution) is the secret sauce that keeps businesses running smoothly. Whether it’s managing customer orders, pricing, shipping, or billing, SAP SD is the backbone of sales o

SAP FICO in 2025: Salary, Jobs & How to Get Certified
AP FICO professionals earn $90,000–$130,000/year in the USA and Canada—and demand is skyrocketing! If you’re eyeing a future-proof IT career, SAP FICO (Financial Accounting & Controlling) is your golden ticket. But where do you start? Sulekha IT Serv

Train Like an AI Engineer: The Smartest Career Move You’ll Make This Year!
Why AI Engineering Is the Hottest Skillset Right Now From self-driving cars to chatbots that sound eerily human, Artificial Intelligence is no longer science fiction — it’s the backbone of modern tech. And guess what? Companies across the USA and Can
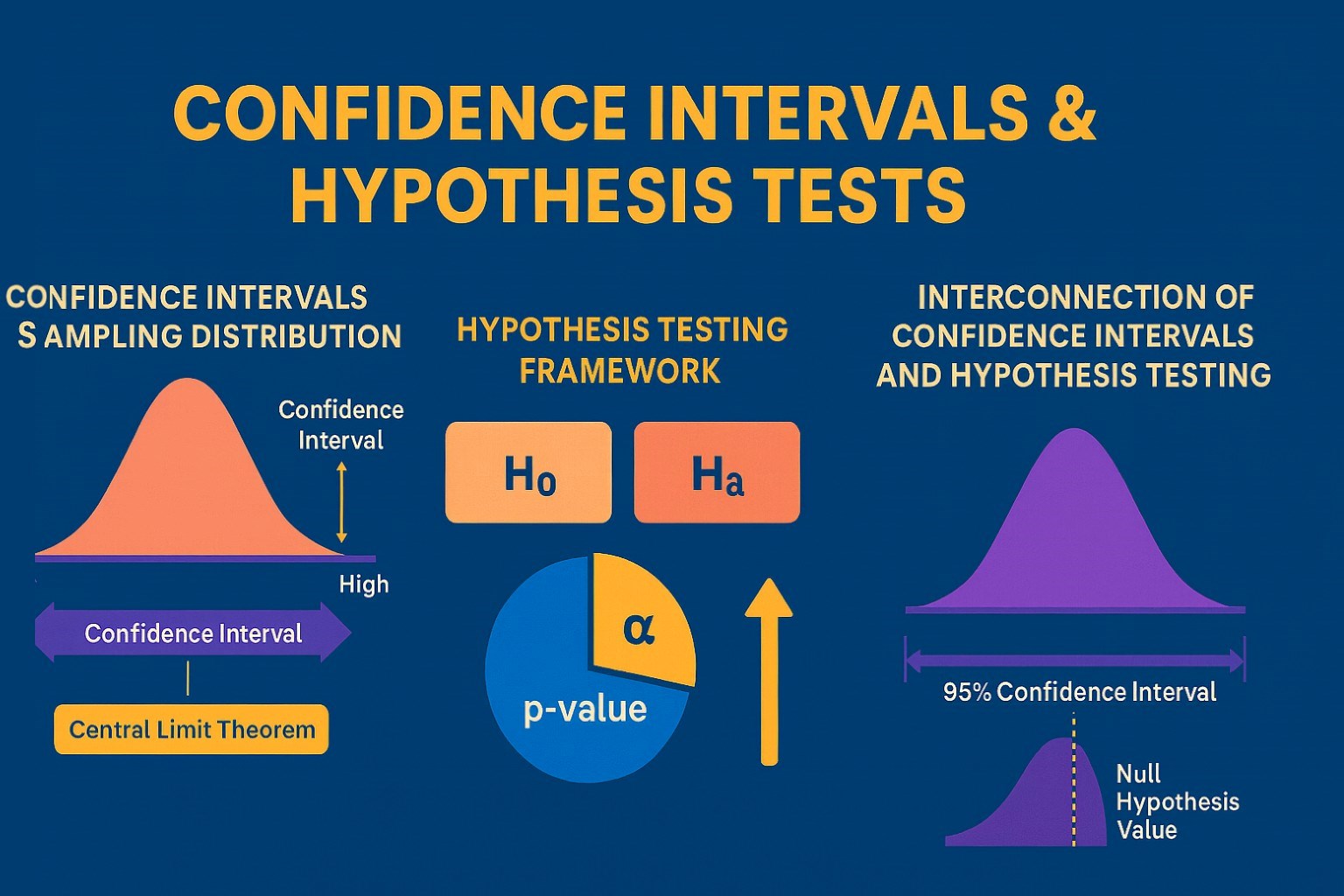
Confidence Intervals & Hypothesis Tests: The Data Science Path to Generalization
Learn how confidence intervals and hypothesis tests turn sample data into reliable population insights in data science. Understand CLT, p-values, and significance to generalize results, quantify uncertainty, and make evidence-based decisions.