What is Network security monitoring?

Network Security Monitoring (NSM) is widely explored by experts around the world who insists on achieving data protection and security across the internet. There are various projects based on the Network Security Monitoring is carried out by top leading research organization. NSM is not an IDS, although it relies on IDS-like products as part of an integrated data collection and analysis suite. NSM involves collecting the full spectrum of data types (event, session, full content and statistical) needed to identify and validate intrusions, explains Richard.
NSM is more concerned with network auditing than with real-time identification of intrusions. Although encryption denies the analyst the ability to see packet contents, it doesn't deny analysts the ability to see traffic patterns. Simply knowing who talked to whom, and when, is more information than most enterprises are collecting today.
The Bro Network Security Monitor provides defenders with visibility into all the machines on a network, the ability to tap into network traffic and examine network packets, and analyzers to examine the application layer. Defenders use Bro's domain-specific scripting language to create site-specific monitoring policies. According to the project website, Bro is used heavily in scientific environments such as universities, research labs, and supercomputing centers.
OSSEC combines a host-based intrusion detection system with log monitoring and SIEM (security information and event management) capabilities for a range of platforms, including Linux, Mac OS, Solaris, AIX, and Windows. Security teams use OSSEC for log analysis, file integrity checking, policy monitoring, rootkit detection, real-time alerts, and active response. Organizations can meet compliance requirements by configuring OSSEC to send alerts about unauthorized file system modifications and malicious behavior embedded in the software logs.
Moloch is a large-scale, full-packet-capturing indexing and database system that helps security teams with incident handling, network security monitoring, and digital forensics. Moloch complements existing intrusion detection systems by providing administrators with a way to browse, search, and export all captured network traffic. The system consists of a single-threaded C application to capture traffic data, a Node.js application to handle the user interface, and an Elasticsearch database.
Choose a training provider to learn IT courses
Java training | J2EE training | J2EE Jboss training | Apache JMeter trainingTake the next step towards your professional goals in Information Technology
Don't hesitate to talk with our course advisor right now
Receive a call
Contact NowMake a call
+1-732-338-7323Related blogs on General to learn more

What is network security Monitoring? A complete guide
In the digital world, we have been using the cloud to store our confidential data to register our details; it can be forms, applications, or product purchasing platforms like e-commerce sites. Though digital platforms have various advantages, one pri

A Guide to Networking Skills: Key Traits for Effective Communication
We have basic networking knowledge but need to know how they pay for a lucrative career or how that works. A network connects two or more services to facilitate effective communication and exchange of information or data via various forms. In the pre

10 Popular System Administrator Certifications To Consider
In the ever-evolving tech landscape, the journey of a System Administrator is one of perpetual learning. Due to this, the demand for system administrator certifications proliferates as organizations seek validated expertise in managing complex IT inf

How CCNA certification helps the networking professional in career?
Networking career being one of the evergreen career with high career scope also engages certain requirements from the candidate. Certification is one of the most important one.

Incident response and forensics
Handling the security breaches over the computer network and system is a challenging and head-breaking task for computer architects.

What Is The Difference Between The CCNA And CCNP Certifications?
Cisco is a major producer of routers and switches that are employed in setting up a dependable and efficient network. To help the clients to choose the personnel who are capable of working with their hardware, it has established a set of certificatio

The Roadmap to Networking Career Opportunities with CISCO
The CCNA (Cisco Certified Network Associate) certification is globally recognized, as it concentrates on developing the role-based models to match the fast deployment of technologies in the modern sophisticated networking environment. Most of the ent

Learning CCNA? – Things to Keep in Mind
Certified Cisco Network Associate (CCNA) is a certification course provided by Cisco, which is the market leading vendor of the IT industry. This certification validates the ability, skill and prowess of an individual to configure, fix and troublesho

Reasons Why CCNA Certification Has an Edge Over Other Certifications
The CCNA (Cisco Certified Network Associate) certification along with the CCNP and CCIE are considered to be the most popular and sought after certifications in the IT industry. The CISCO Systems awards both dedicated and general certifications to ca

Why The Value Of CCNA Certification Is On Constant Rise?
The CCNA (Cisco Certified Network Associate) certification is emerging as the most popular IT certification in the world, as it focuses on developing role-based models to match the swift deployment of technologies in the modern sophisticated networki
Latest blogs on technology to explore

From Student to AI Pro: What Does Prompt Engineering Entail and How Do You Start?
Explore the growing field of prompt engineering, a vital skill for AI enthusiasts. Learn how to craft optimized prompts for tools like ChatGPT and Gemini, and discover the career opportunities and skills needed to succeed in this fast-evolving indust

How Security Classification Guides Strengthen Data Protection in Modern Cybersecurity
A Security Classification Guide (SCG) defines data protection standards, ensuring sensitive information is handled securely across all levels. By outlining confidentiality, access controls, and declassification procedures, SCGs strengthen cybersecuri

Artificial Intelligence – A Growing Field of Study for Modern Learners
Artificial Intelligence is becoming a top study choice due to high job demand and future scope. This blog explains key subjects, career opportunities, and a simple AI study roadmap to help beginners start learning and build a strong career in the AI

Java in 2026: Why This ‘Old’ Language Is Still Your Golden Ticket to a Tech Career (And Where to Learn It!
Think Java is old news? Think again! 90% of Fortune 500 companies (yes, including Google, Amazon, and Netflix) run on Java (Oracle, 2025). From Android apps to banking systems, Java is the backbone of tech—and Sulekha IT Services is your fast track t
From Student to AI Pro: What Does Prompt Engineering Entail and How Do You Start?
Learn what prompt engineering is, why it matters, and how students and professionals can start mastering AI tools like ChatGPT, Gemini, and Copilot.

Cyber Security in 2025: The Golden Ticket to a Future-Proof Career
Cyber security jobs are growing 35% faster than any other tech field (U.S. Bureau of Labor Statistics, 2024)—and the average salary is $100,000+ per year! In a world where data breaches cost businesses $4.45 million on average (IBM, 2024), cyber secu

SAP SD in 2025: Your Ticket to a High-Flying IT Career
In the fast-paced world of IT and enterprise software, SAP SD (Sales and Distribution) is the secret sauce that keeps businesses running smoothly. Whether it’s managing customer orders, pricing, shipping, or billing, SAP SD is the backbone of sales o

SAP FICO in 2025: Salary, Jobs & How to Get Certified
AP FICO professionals earn $90,000–$130,000/year in the USA and Canada—and demand is skyrocketing! If you’re eyeing a future-proof IT career, SAP FICO (Financial Accounting & Controlling) is your golden ticket. But where do you start? Sulekha IT Serv

Train Like an AI Engineer: The Smartest Career Move You’ll Make This Year!
Why AI Engineering Is the Hottest Skillset Right Now From self-driving cars to chatbots that sound eerily human, Artificial Intelligence is no longer science fiction — it’s the backbone of modern tech. And guess what? Companies across the USA and Can
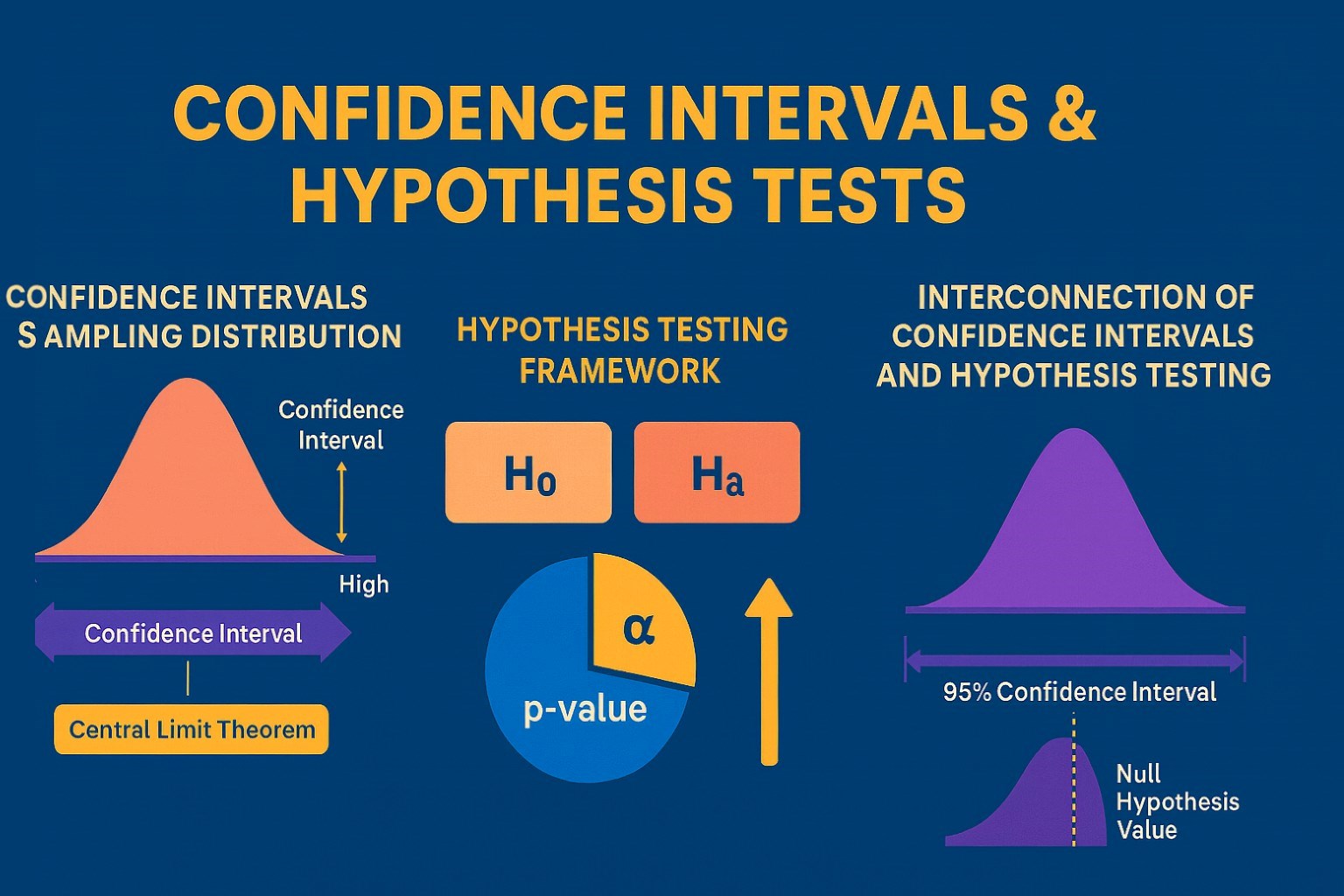
Confidence Intervals & Hypothesis Tests: The Data Science Path to Generalization
Learn how confidence intervals and hypothesis tests turn sample data into reliable population insights in data science. Understand CLT, p-values, and significance to generalize results, quantify uncertainty, and make evidence-based decisions.