Skills Roadmap - Tailoring Growth to Your Professional Journey in Cybersecurity
The pursuit of knowledge and skills is paramount in the ever-evolving landscape of Cybersecurity, where the digital world meets the real world. Whether you are an experienced professional or just starting out, your journey in Cybersecurity is unique and deserves a strategic approach. It is a personalized guide designed to help you chart a course through the intricacies of the cybersecurity field. Whether you're a seasoned security professional or just beginning to explore this fascinating domain, this roadmap will help you align your skill development with your cybersecurity aspirations.
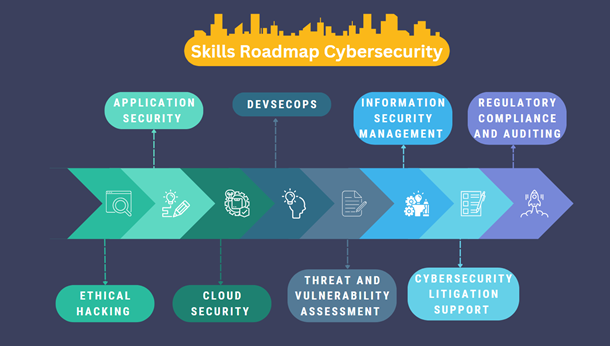
The following is a breakdown of some skills that help start your career and shine in Cybersecurity.
Ethical hacking skills:
Ethical hacking is also called penetration testing. Ethical hacking skills are considered the most sought-after skills in various industries and by H.R. managers. Moreover, various private institutions offer an ethical hacking course, which is best for beginners. The best institution covers basic to advanced hacking concepts and provides hands-on training.
So, those who intend to become ethical hackers can join the certification course to boost their careers and aid them in getting into the cybersecurity world.
This certification course will not better suit professionals and experts already in the I.T. world, including I.T. officers, because they can get into higher positions with better remuneration in various organizations.
However, those experts have different certification levels to pursue advanced cybersecurity careers.
Application security skills:
As the name of the title implies, application security is the process and verification to ensure the application is safe and protected. By utilizing ERP software and other customized solutions for business, it is possible to secure the application.
So, those who intend to begin their career in application security must acquire application security skills for entry-level positions in Cybersecurity.
Before entering this entry-level position, beginners must be conversant in app development. Taking an application security course will improve every chance of getting into better-paid jobs in the cyber security industry.
If you are experienced, then you should look for better security-related courses. If you are from a non-technical field, this course is a learning curve in I.T.
Cloud security skills
We might have heard people saying the cloud is an old technology, but without the cloud, we cannot Voice over the Internet. But it has already reached the peak of the most demanding career path in I.T.
Those in the cloud field will be tech-savvy and have strong technical skills. If you choose the cloud field, you should strongly understand cloud security because it is a booming career in the IT sector.
After completing the Cloud security course, you can land a career as a cloud architect and app developer. Those who are experienced will have advanced skills and demand high remuneration.
Beginners who have entered this field with a single certification in cloud security cannot secure job positions; instead, they should have continuous learning and pursue next-level certification.
DevSecOps skills:
DevOps is a software development phase in which development and IT operations are integrated. It attempts to eliminate the individualistic perceptions of departments as autonomous entities in organizations and ensure that business units function as a team.
It facilitates departmental collaboration, which frequently entails integrating business processes and exchanging data. However, DevOps exposes firms to extra risks because the dangers in one department are spread throughout the entire company.
Risks like app vulnerabilities are minimized during development due to DevSecOps. As a result, security measures to protect enterprise-wide apps are put in place during development. Most experienced DevOps experts align with DevSecOps. The necessary DevOps training could advance a professional's career and open doors to work in higher-level roles like project managers.
Threat and vulnerability assessment skills
Threat and vulnerability assessment skills will help you identify the threats and weaknesses of organizations. These skills will help solve complex problems quickly.
If you are a beginner or professional, both must have the technical skills of threat and vulnerability assessment. So, if you are a beginner, taking this certification course will help you learn from basic to advanced concepts and aid you in getting into a stable career path in Cybersecurity.
Organizations provide better opportunities for people skilled in threat and vulnerability assessment. Those with these skills can be a Chief Information Security and Technology Officer.
Information security management skills:
IT security management is considered an essential skill. These skills help you collect, process, and store information to protect the data securely. To acquire these skills, you can join an IT security management-related course and learn fundamental to advanced concepts.
If you are experienced and intend to take this certification course, you can join ISM, which is the best choice to get executive positions in the organization relating to security. These positions include CISO and CTO.
Cybersecurity litigation support skills:
Organizations now require the services of legal professionals to assist with any potential legal actions that may be taken, such as lawsuits related to Cybersecurity or when an organization is sued.
However, to have the requisite skills to litigate cybersecurity disputes, standard lawyers may need to take some training or require more cybersecurity knowledge. Beginners must be better suited for this course since they need more legal and Cybersecurity understanding.
Regulatory compliance and auditing skills:
We have seen many acts and laws passed to manage cyber-attacks in different regions of the world. Organizations need help to assess whether they have obtained all of these.
For example, federal and state laws and regulations in the U.S. govern the sale and consumption of alcohol, such as the Federal Alcohol Administration Act (FAA Act) and various state alcohol control laws.
The E.U. passed GDPR and governs how businesses must disclose to users how they collect, employ, share, and secure their data. There are numerous other rules in addition to these.
Each has a set of consequences if they are not followed. To ensure that firms are determined to be fully compliant with all relevant legislation, the auditors who are more familiar with the standards of compliance are sought-after and demanding in the cybersecurity industry.
In conclusion, "Cybersecurity is not just a profession; it's a mission to protect, secure, and innovate in an increasingly interconnected world. As you set out on your cybersecurity journey, remember that your skills are your compass, guiding you through the digital wilderness. Our 'Skills Roadmap' is your trusted companion, helping you navigate the ever-evolving landscape of Cybersecurity, regardless of your career. As you embark on this path, rest assured that your growth is tailored to your unique professional journey.
So, keep learning and adapting, whether you're thwarting threats, safeguarding data, or fortifying digital fortresses. Your expertise is the shield that guards against the digital unknown. Welcome to the world of Cybersecurity, where every skill you acquire is a step towards a safer and more secure digital future.
Find a course provider to learn Cyber Security
Java training | J2EE training | J2EE Jboss training | Apache JMeter trainingTake the next step towards your professional goals in Cyber Security
Don't hesitate to talk with our course advisor right now
Receive a call
Contact NowMake a call
+1-732-338-7323Take our FREE Skill Assessment Test to discover your strengths and earn a certificate upon completion.
Enroll for the next batch
Cyber Security Online Training
- Dec 17 2025
- Online
Cyber Security Online Training
- Dec 18 2025
- Online
Cyber Security Online Training
- Dec 19 2025
- Online
Related blogs on Cyber Security to learn more

How Security Classification Guides Strengthen Data Protection in Modern Cybersecurity
A Security Classification Guide (SCG) defines data protection standards, ensuring sensitive information is handled securely across all levels. By outlining confidentiality, access controls, and declassification procedures, SCGs strengthen cybersecuri

What Is a Security Classification Guide in Cybersecurity?
A Security Classification Guide (SCG) defines how to categorize information assets by sensitivity, with clear instructions from authorized officials to ensure consistent, compliant data handling.

Cybersecurity Training: Powering Digital Defense
Explore top cybersecurity training programs in the USA to meet rising demand in digital defense. Learn about certifications, salaries, and career opportunities in this high-growth field.

What Does a Cybersecurity Analyst Do? 2025
Discover the vital role of a Cybersecurity Analyst in 2025, protecting organizations from evolving cyber threats through monitoring, threat assessment, and incident response. Learn about career paths, key skills, certifications, and why now is the be

What essential skills and trends should cybersecurity professionals navigate in 2024?
Cybersecurity professionals in 2024 must master a diverse skillset, from cloud security and AI to soft skills like communication and problem-solving, to stay ahead of evolving cyber threats and regulations.

What Does a Cybersecurity Analyst Do?
Learn about the role of a Cybersecurity Analyst, responsible for protecting an organization's computer networks from cyberattacks.

10 Popular Cybersecurity Certifications
From CompTIA Security+ to CISSP, these certifications can boost your career and demonstrate your commitment to protecting computer systems and networks.

What are the most popular technical certifications for future career advancement?
Unlock your potential with insights into 5 popular technical certifications for future career growth, spanning cybersecurity, blockchain, cloud computing and more. Explore pathways for professional advancement today.

How to Become a Security Architect: 2024 Career Guide
How to Become a Security Architect: 2024 Career Guide In today's fast-paced and digitally interconnected world, the role of a Security Architect
Latest blogs on technology to explore

From Student to AI Pro: What Does Prompt Engineering Entail and How Do You Start?
Explore the growing field of prompt engineering, a vital skill for AI enthusiasts. Learn how to craft optimized prompts for tools like ChatGPT and Gemini, and discover the career opportunities and skills needed to succeed in this fast-evolving indust

How Security Classification Guides Strengthen Data Protection in Modern Cybersecurity
A Security Classification Guide (SCG) defines data protection standards, ensuring sensitive information is handled securely across all levels. By outlining confidentiality, access controls, and declassification procedures, SCGs strengthen cybersecuri

Artificial Intelligence – A Growing Field of Study for Modern Learners
Artificial Intelligence is becoming a top study choice due to high job demand and future scope. This blog explains key subjects, career opportunities, and a simple AI study roadmap to help beginners start learning and build a strong career in the AI

Java in 2026: Why This ‘Old’ Language Is Still Your Golden Ticket to a Tech Career (And Where to Learn It!
Think Java is old news? Think again! 90% of Fortune 500 companies (yes, including Google, Amazon, and Netflix) run on Java (Oracle, 2025). From Android apps to banking systems, Java is the backbone of tech—and Sulekha IT Services is your fast track t
From Student to AI Pro: What Does Prompt Engineering Entail and How Do You Start?
Learn what prompt engineering is, why it matters, and how students and professionals can start mastering AI tools like ChatGPT, Gemini, and Copilot.

Cyber Security in 2025: The Golden Ticket to a Future-Proof Career
Cyber security jobs are growing 35% faster than any other tech field (U.S. Bureau of Labor Statistics, 2024)—and the average salary is $100,000+ per year! In a world where data breaches cost businesses $4.45 million on average (IBM, 2024), cyber secu

SAP SD in 2025: Your Ticket to a High-Flying IT Career
In the fast-paced world of IT and enterprise software, SAP SD (Sales and Distribution) is the secret sauce that keeps businesses running smoothly. Whether it’s managing customer orders, pricing, shipping, or billing, SAP SD is the backbone of sales o

SAP FICO in 2025: Salary, Jobs & How to Get Certified
AP FICO professionals earn $90,000–$130,000/year in the USA and Canada—and demand is skyrocketing! If you’re eyeing a future-proof IT career, SAP FICO (Financial Accounting & Controlling) is your golden ticket. But where do you start? Sulekha IT Serv

Train Like an AI Engineer: The Smartest Career Move You’ll Make This Year!
Why AI Engineering Is the Hottest Skillset Right Now From self-driving cars to chatbots that sound eerily human, Artificial Intelligence is no longer science fiction — it’s the backbone of modern tech. And guess what? Companies across the USA and Can
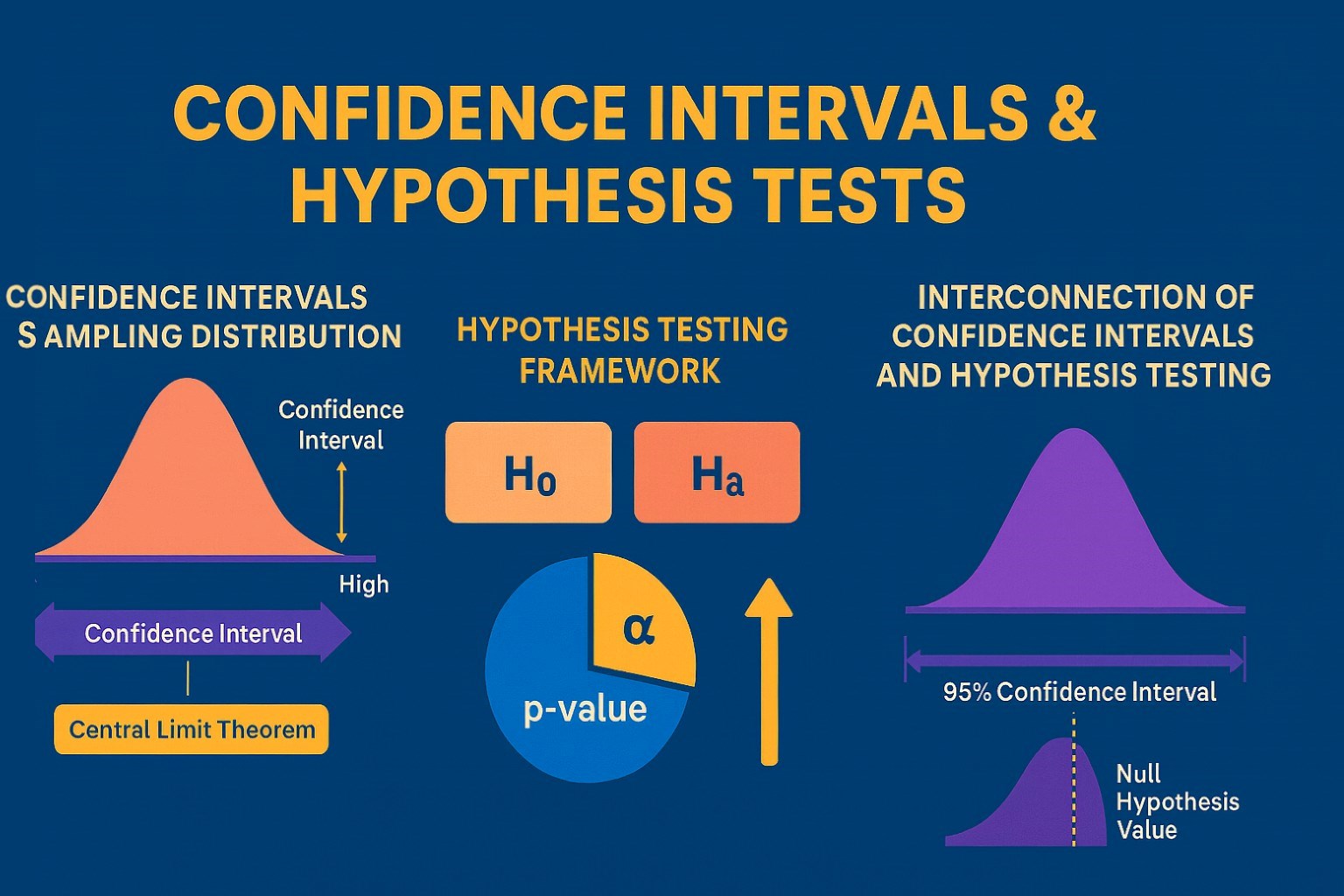
Confidence Intervals & Hypothesis Tests: The Data Science Path to Generalization
Learn how confidence intervals and hypothesis tests turn sample data into reliable population insights in data science. Understand CLT, p-values, and significance to generalize results, quantify uncertainty, and make evidence-based decisions.
