Security concerns to think about in IoT
According to Evans Data’s recent Internet of Things Development survey, at least 31% of the software developers engaged in creating applications for IoT devices cite serious security concerns in the software that will run devices.
Security has always remained of paramount importance in the data driven environment. However, in the IoT stream, security concerns weigh manifold times than traditional desktop or mobile devices.
The extent of damage that will be incurred in the cause of a security breach in the IoT environment is far more serious and impactful than in other scenarios.
In addition to loss of personal data, the security breach may also potentially cause serious safety concerns since home appliances are also forming part of the IoT environment.
What causes the difference in security between IoT and other mediums?
Traditional devices like desktops, mobiles, hybrid devices, etc. are programmed to thwart hacking attempts or unauthorized infiltrations using perimeter defense networks.
However, when it comes to protecting user privacy and data confidentiality in IoT devices, these perimeter network defense systems are acutely inadequate.
In the IoT realm, hackers can attempt to break into private networks even through the Radio Frequency medium.
Which means, any device that is activated with 2G, 3G or 4G networks, Bluetooth, ZigBee, Radio Frequency Identification (RFID) or NFC will be susceptible for third party hacking.
IoT will create a trillion and more open-to-attack data points
Every single IoT device can be counted as hack-prone. There is no way that manufacturers of these devices can confirm that the data collected and streamed are secure at all times. The present lack of a standard security IoT protocol only establishes this fact.
In case of a security breach, the ultimate security challenge will be to contain the data loss to a single or short range of devices without letting it spread to the whole set of interconnected devices.
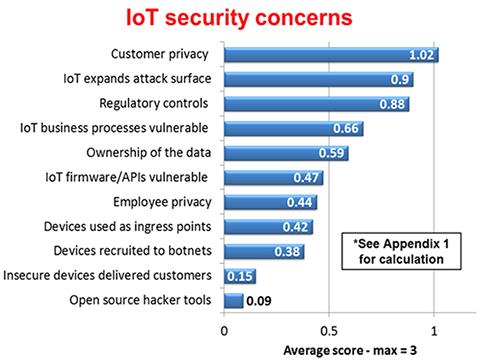
The below mentioned chart depicts how much severe certain areas of privacy and user information are in IoT.
How can security risks in IoT be mitigated?
Aligning vendors to a common security protocol
Secondly, vendors of IoT devices should coordinate their efforts to plug possible security issues right at the manufacturing stage. IoT typically contains multiple vendors. Too many appliance and device manufacturers will be aligning their devices together to work in conjunction on short-distance networks like BLE, RFID, NFC, etc. This potentially gives hackers multiple entry points to target and launch a breach action.
“Gartner Says 6.4 Billion Connected "Things" Will Be in Use in 2016 and more than 5.5 million new things will get connected every day.”
Hence, it is too late to roll out a common security protocol for all devices. However, it is still plausible to standardize the security protocols which will stave off possible security concerns in the near future. It will give rise to a new breed of IoT devices which will be hack-proof and adhering to single authority of security protocol.
Training IT security experts
There are several layers to dealing with the security concerns in IoT. However, broadly it originates with the training and development of system security officers who are working in the IoT environment.
Developers must be trained in coding software and firmware for IoT devices using various control measures including: context-aware access control, real-time security analytics, endpoint threat detection, cloud access security, etc.
Creating awareness amidst end users
In every crisis and threat prone situation, the maximum coverage can be done only at the end point, which in IoT is the end user.
Users must be enlightened about the possible security threats like Ransomware, DDoS attacks, Spyware, etc. which can possibly attack not only their computer systems, but in the near IoT enabled future, even their home appliances.
The extent of damage that can be caused as a result of security breach and privacy invasion must also be made aware to the end users.
Find a course provider to learn Cyber Security
Java training | J2EE training | J2EE Jboss training | Apache JMeter trainingTake the next step towards your professional goals in Cyber Security
Don't hesitate to talk with our course advisor right now
Receive a call
Contact NowMake a call
+1-732-338-7323Take our FREE Skill Assessment Test to discover your strengths and earn a certificate upon completion.
Enroll for the next batch
hands on cyber security training
- Sep 1 2025
- Online
cyber security classes online
- Sep 2 2025
- Online
hands on cyber security training
- Sep 3 2025
- Online
Cyber Security
- Sep 4 2025
- Online
hands on cyber security training
- Sep 5 2025
- Online
Related blogs on Cyber Security to learn more

Cybersecurity Training: Powering Digital Defense
Explore top cybersecurity training programs in the USA to meet rising demand in digital defense. Learn about certifications, salaries, and career opportunities in this high-growth field.

What Does a Cybersecurity Analyst Do? 2025
Discover the vital role of a Cybersecurity Analyst in 2025, protecting organizations from evolving cyber threats through monitoring, threat assessment, and incident response. Learn about career paths, key skills, certifications, and why now is the be

What essential skills and trends should cybersecurity professionals navigate in 2024?
Cybersecurity professionals in 2024 must master a diverse skillset, from cloud security and AI to soft skills like communication and problem-solving, to stay ahead of evolving cyber threats and regulations.

What Does a Cybersecurity Analyst Do?
Learn about the role of a Cybersecurity Analyst, responsible for protecting an organization's computer networks from cyberattacks.

10 Popular Cybersecurity Certifications
From CompTIA Security+ to CISSP, these certifications can boost your career and demonstrate your commitment to protecting computer systems and networks.

What are the most popular technical certifications for future career advancement?
Unlock your potential with insights into 5 popular technical certifications for future career growth, spanning cybersecurity, blockchain, cloud computing and more. Explore pathways for professional advancement today.

How to Become a Security Architect: 2024 Career Guide
How to Become a Security Architect: 2024 Career Guide In today's fast-paced and digitally interconnected world, the role of a Security Architect

Tips to get a job in top companies - Find out about the strategy and preparation to get started with Cybersecurity
As companies adopt cloud services, IoT devices, and remote work solutions, their attack surface expands. Cybersecurity experts are essential to ensure the security of these technologies and networks. The expertise of cybersecurity specialists bolster

Types of certification path in cyber security
Pursuing certification courses in cybersecurity is considered mandatory due to several compelling reasons. Firstly, the ever-evolving nature of cyber threats demands that cybersecurity professionals stay updated with the latest knowledge and skills.
Latest blogs on technology to explore

Understanding Artificial Intelligence: Hype, Reality, and the Road Ahead
Explore the reality of Artificial Intelligence (AI) — its impact, how it works, and its potential risks. Understand AI's benefits, challenges, and how to navigate its role in shaping industries and everyday life with expert training programs

How Much Do Healthcare Administrators Make?
Discover how much healthcare administrators make, the importance of healthcare, career opportunities, and potential job roles. Learn about salary ranges, career growth, and training programs with Sulekha to kickstart your healthcare administration jo

How to Gain the High-Income Skills Employers Are Looking For?
Discover top high-income skills like software development, data analysis, AI, and project management that employers seek. Learn key skills and growth opportunities to boost your career.

What Companies Expect from Product Managers in 2025: Skills, Tools, and Trends
Explore what companies expect from Product Managers in 2025, including essential skills, tools, certifications, and salary trends. Learn how to stay ahead in a rapidly evolving, tech-driven product management landscape.

Breaking Into AI Engineering: Skills, Salaries, and Demand in the US
Discover how to break into AI engineering with insights on essential skills, salary expectations, and rising demand in the US. Learn about career paths, certifications, and how to succeed in one of tech’s fastest-growing fields.

Cybersecurity Training: Powering Digital Defense
Explore top cybersecurity training programs in the USA to meet rising demand in digital defense. Learn about certifications, salaries, and career opportunities in this high-growth field.

Why Pursue Data Science Training?
Empower your career in a data-driven world. Learn why data science training is crucial for high-demand jobs, informed decisions, and staying ahead with essential skills.

What Does a Cybersecurity Analyst Do? 2025
Discover the vital role of a Cybersecurity Analyst in 2025, protecting organizations from evolving cyber threats through monitoring, threat assessment, and incident response. Learn about career paths, key skills, certifications, and why now is the be

Artificial intelligence in healthcare: Medical and Diagnosis field
Artificial intelligence in healthcare: Medical and Diagnosis field

iOS 18.5 Is Here: 7 Reasons You Should Update Right Now
In this blog, we shall discuss Apple releases iOS 18.5 with new features and bug fixes
- Cyberark
- Penetration Testing
- Cyber Security
- ISC–Certified In Cybersecurity
- IT User Support Specialist
- Information Security Manager
- CISM
- CEH
- Security Architect
- Ultimate Online Cybersecurity Training Series
- Cybersecurity Essentials Protecting Yourself In The Digital Age
- CompTIA PenTest + PT0-001 Master Pentesting
