How Effective Is Oracle Identity Manager Deployment Model?
Oracle Identity Manager is a completely integrated, a super advanced next-generation identity management platform that enables organizations to breakthrough scalability and keep up the pace with the compliance of regulatory mandates. The identity manager helps to secure sensitive data and applications regardless of their location of hosting and helps to keep the operational costs exceedingly low. Oracle Identity Governance includes Oracle Identity Analytics, Oracle Identity Manager, and Oracle Privileged Account Manager.
Oracle Identity Manager Deployment Model (OIM)
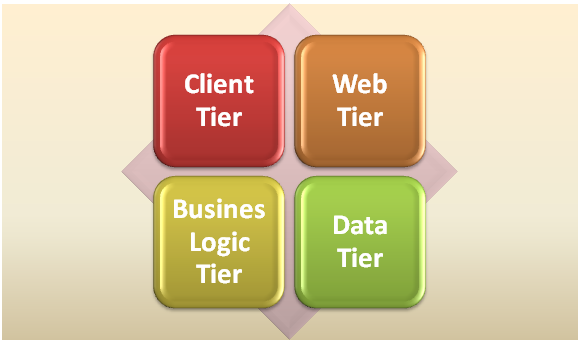
In Oracle identity management every component of the application including design, core server engine and web application is written in Java and is executed using a multi-tier deployment model. The entire framework can be divided into four separate parts known as client tier, web tier, business tier and data tier.
Client Tier – In oracle identity manager usually two types of clients are used, namely web-based administrator and design based administrator console. The web based console is used for managing the usage of resources and all other constructs that accompany them. The development model on the other end of the spectrum is used by developers for the purpose of identity management. Its main function is to design and configure the core components like resource objects, provisioning processes, IT sources and to integrate the configurations so that communication can be enabled with physical applications. Both the models are capable of handling clients from many computers with similar policies defined in the OIM business logic tier.
Web Tier – The web tier is often used as a web application container for OIM user interface. The web tier is entirely written Java and uses technologies like JSP, JavaBeans and Struts. By using a host of different technologies the web tier can be deployed in numerous server applications and containers.
Business Logic Tier – This is the most important tier in the oracle identity manager deployment model. In this tier the provision of the user is determined including the target resource and the process. This tier leverages J2EE leverage pattern and is written using the Java language exclusively which gives it the benefit of platform neutrality and distributed component architecture. The business tier allows standard deployment platform for the integration of adapters and connectors. Given the inherent distributed nature of J2EE, the business tier enjoys the benefit of being spread across multiple server deployments while having access to common metadata from the data tier.
Data Tier– The data tier is primarily known as the relationship database whose main function is to store all data about access, identities and provisions for user end platforms. Only the data from the Java archive files which houses the code to connect to third party target system and resources is not included in this tier. The business tier has the exclusive rights of accessing the data tier. Any external tools and clients are strictly prohibited from entering this tier. Many organizations use database protection technologies like Oracle Database Vault and Transparent Data Encryption to keep their data safe and protected.
Oracle Identity manager has the ability to blend rich user experience along with extreme scalability. It is in fact one of the best in class suit for identity management solutions. It helps to secure access from all types of devices both within and beyond the firewall. It also helps to streamline self-service and audit reports which help an organization to make considerable savings.
While working on relatively less secure devices like mobile and tablets oracle provides a mobile security suite which has helped to build a feature rich cross platform for integrated applications. It also provides users with a comprehensive platform for account administration and account management. It helps to simplify the entire process and creates opportunities for tapping into the future possibilities. The software is operational with a wide range of different kind of operating system and hardware providing the user with maximum flexibility.
Take the next step towards your professional goals in Oracle Identity Manager
Don't hesitate to talk with our course advisor right now
Receive a call
Contact NowMake a call
+1-732-338-7323Related blogs on Oracle Identity Manager to learn more

How To Secure Your Sensitive Data With Oracle’s Identity Manager User Provisioning?
Organizations like human beings are dynamic in nature and as they grow a lot of changes take place, which include new system interfaces, applications and resources. The attrition rate in most of the companies is quite high and it is a big headache f
Latest blogs on technology to explore

Drug Safety & Pharmacovigilance: Your 2026 Career Passport to a Booming Healthcare Industry!
Why This Course Is the Hottest Ticket for Science Grads & Healthcare Pros (No Lab Coat Required!)" The Exploding Demand for Drug Safety Experts "Did you know? The global pharmacovigilance market is set to hit $12.5B by 2026 (Grand View Research, 202

Launch Your Tech Career: Why Mastering AWS Foundation is Your Golden Ticket in 2026
There’s one skill that can open all those doors — Amazon Web Services (AWS) Foundation

Data Science in 2026: The Hottest Skill of the Decade (And How Sulekha IT Services Helps You Master It!)
Data Science: The Career that’s everywhere—and Nowhere Near Slowing Down "From Netflix recommendations to self-driving cars, data science is the secret sauce behind the tech you use every day. And here’s the kicker: The U.S. alone will have 11.5 mill

Salesforce Admin in 2026: The Career Goldmine You Didn’t Know You Needed (And How to Break In!)
The Salesforce Boom: Why Admins Are in Crazy Demand "Did you know? Salesforce is the 1 CRM platform worldwide, used by 150,000+ companies—including giants like Amazon, Coca-Cola, and Spotify (Salesforce, 2025). And here’s the kicker: Every single one

Python Power: Why 2026 Belongs to Coders Who Think in Python
If the past decade was about learning to code, the next one is about coding smarter. And in 2026, the smartest move for any IT enthusiast is learning Python — the language that powers AI models, automates the web, and drives data decisions across ind

The Tableau Revolution of 2025
"In a world drowning in data, companies aren’t just looking for analysts—they’re hunting for storytellers who can turn numbers into decisions. Enter Tableau, the #1 data visualization tool used by 86% of Fortune 500 companies (Tableau, 2024). Whether

From Student to AI Pro: What Does Prompt Engineering Entail and How Do You Start?
Explore the growing field of prompt engineering, a vital skill for AI enthusiasts. Learn how to craft optimized prompts for tools like ChatGPT and Gemini, and discover the career opportunities and skills needed to succeed in this fast-evolving indust

How Security Classification Guides Strengthen Data Protection in Modern Cybersecurity
A Security Classification Guide (SCG) defines data protection standards, ensuring sensitive information is handled securely across all levels. By outlining confidentiality, access controls, and declassification procedures, SCGs strengthen cybersecuri

Artificial Intelligence – A Growing Field of Study for Modern Learners
Artificial Intelligence is becoming a top study choice due to high job demand and future scope. This blog explains key subjects, career opportunities, and a simple AI study roadmap to help beginners start learning and build a strong career in the AI

Java in 2026: Why This ‘Old’ Language Is Still Your Golden Ticket to a Tech Career (And Where to Learn It!
Think Java is old news? Think again! 90% of Fortune 500 companies (yes, including Google, Amazon, and Netflix) run on Java (Oracle, 2025). From Android apps to banking systems, Java is the backbone of tech—and Sulekha IT Services is your fast track t